WordPress Security: Advanced Techniques and Best Practices (with Sample Code)
Table of Contents
WordPress powers a vast number of websites around the world, and its user-friendly nature has made it a favorite for everyone from small business owners to large corporations. However, its popularity also makes it an attractive target for cyber threats. If you’re managing a WordPress site, securing it isn’t just a recommendation—it’s a necessity.
In this post, we’ll dive into advanced strategies and essential best practices to strengthen your WordPress site’s defenses. Implementing these measures will help you maintain a secure and trustworthy online presence.
Common WordPress Vulnerabilities
Let’s take a closer look at some of the key vulnerabilities that frequently affect WordPress sites:
- SQL Injection: This attack injects malicious code into your website’s database, allowing hackers to access or manipulate sensitive information. The consequences can be severe, putting your site’s integrity at serious risk.
- Cross-Site Scripting (XSS): XSS attacks occur when harmful scripts are injected into your website, running on your users’ browsers. This not only jeopardizes user data but also damages your site’s reputation.
- Brute Force Attacks: These attacks involve automated tools that repeatedly attempt to guess your passwords until they get it right. Without proper defenses, it’s only a matter of time before they succeed.
- Plugin and Theme Vulnerabilities: Not all plugins and themes are built with security in mind. Outdated or poorly coded ones can introduce significant security holes, making your site an easy target.
- File Upload Vulnerabilities: Allowing users to upload files can be a useful feature, but it also opens the door for attackers to upload malicious files. If not properly secured, this can lead to serious breaches.
Core WordPress Security Best Practices
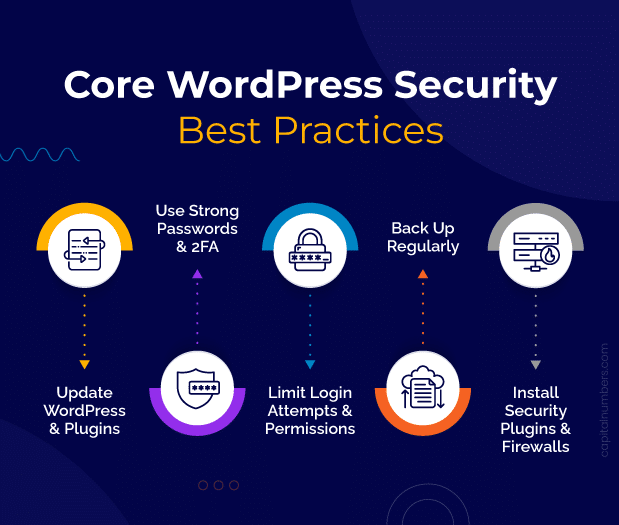
1. Keeping WordPress and Plugins Up-to-Date
- Regular Updates: One of the simplest yet most effective ways to secure your WordPress site is by keeping everything up to date. This includes the WordPress core, your themes, and all your plugins. Updates frequently contain patches for known vulnerabilities, so staying current is a crucial step in maintaining a secure site.
- Automatic Updates: To streamline the update process and reduce the risk of running outdated software, enable automatic updates for the WordPress core and your plugins. This ensures that critical updates are applied as soon as they’re available, without you having to lift a finger.
2. Using Strong Passwords and Two-Factor Authentication
- Complex Passwords: Strong passwords are a fundamental part of WordPress security. Make sure your passwords are complex—using a mix of uppercase and lowercase letters, numbers, and symbols. Avoid common words or easily guessable information.
- Two-Factor Authentication (2FA): Adding an extra layer of security with Two-Factor Authentication is a no-brainer. 2FA requires a second form of verification, like a code sent to your phone or email, making it much harder for unauthorized users to access your admin account.
3. Limiting Login Attempts and User Permissions
- Failed Login Attempts: Brute force attacks are a common threat to WordPress sites. To counter this, limit the number of failed login attempts. This simple tweak can significantly reduce the risk of unauthorized access.
- User Roles: Not everyone needs full access to your WordPress site. Assign user roles based on the principle of least privilege—only give users the permissions they need to do their job. Reserve administrative privileges for those who truly need them.
- Plugin Permissions: Similarly, review the permissions for your plugins. Ensure that each plugin has only the necessary access to your site’s data. Overly permissive plugins can be a security risk.
4. Regularly Backing Up Your WordPress Site
- Complete Backups: Regular backups are your safety net. Make sure you’re creating full backups of your WordPress site, including both files and databases. If something goes wrong, a backup is the quickest way to get your site back online.
- Off-Site Storage: Store your backups off-site. This way, even if your site is compromised, your backups remain safe and secure. Off-site backups protect against data loss due to hacks, server failures, or other disasters.
5. Installing Security Plugins and Firewalls
- Security Plugins: Enhancing your site’s security is easier with the right tools. Invest in reputable security plugins that can scan for vulnerabilities, block malicious traffic, and provide additional layers of protection.
- Web Application Firewall (WAF): A Web Application Firewall is a strong defense against common web attacks like SQL injection and cross-site scripting. A WAF can filter out malicious requests before they even reach your site, keeping your WordPress installation safe from harm.
Need a WordPress website that’s secure and drives results? Our WordPress Development Services are here to help you succeed.
Advanced Security Techniques for WordPress Websites
1. Hardening the WordPress Installation:
When it comes to WordPress security, it’s all about reducing your attack surface. Here’s how you can harden your WordPress installation:
- File Permissions: Setting the right file permissions is critical. Ensure that your files and directories are only accessible to those who absolutely need access. This minimizes the chances of unauthorized users getting their hands on sensitive information.
- Directory Permissions: Disabling directory browsing is a must. You don’t want curious eyes exploring your site’s file structure and finding potential vulnerabilities. A simple tweak can keep your directories out of sight and out of mind.
- Remove Unused Plugins and Themes: If you’re not using a plugin or theme, it doesn’t belong on your site. Unused plugins and themes are just extra doors for attackers to try and open. Delete them to reduce your risk.
- Hide WordPress Version: Disguising your WordPress version number is a clever way to keep attackers guessing. If they can’t easily identify your version, it’s harder for them to exploit known vulnerabilities.
2. Protecting Against Common Vulnerabilities:
To guard against the most common vulnerabilities, you’ll want to take a proactive approach:
- SQL Injection Prevention: SQL injection is a classic attack, but you can prevent it by using prepared statements or parameterized queries. This simple step can stop attackers from manipulating your database. Here’s an example of SQL Injection prevention in PHP using prepared statements with MySQLi. Prepared statements ensure that user input is treated as data, not executable code.
//======php======== <?php // Database connection $servername = "localhost"; $username = "root"; $password = ""; $dbname = "test_db"; $conn = new mysqli($servername, $username, $password, $dbname); // Check connection if ($conn->connect_error) { die("Connection failed: " . $conn->connect_error); } // Function to fetch user by username (safe from SQL Injection) function getUserByUsername($conn, $username) { // Prepared statement $stmt = $conn->prepare("SELECT * FROM users WHERE username = ?"); // Bind parameters (s = string type) $stmt->bind_param("s", $username); // Execute the query $stmt->execute(); // Get the result $result = $stmt->get_result(); // Fetch the user $user = $result->fetch_assoc(); // Close the statement $stmt->close(); return $user; } // Get user input (for example, from a form) $user_input = $_GET['username']; // Fetch user safely using the prepared statement $user = getUserByUsername($conn, $user_input); if ($user) { echo "User found: " . $user['username']; } else { echo "User not found"; } // Close connection $conn->close(); ?>Explanation:
- Prepared Statements: The “prepare()” function prepares an SQL statement for execution.
- Binding Parameters: “bind_param()” binds the input parameter to the prepared statement. The “s” specifies that the input is a string.
- Safe Execution: The input from the user is safely handled, even if the user enters malicious input like “’; DROP TABLE users;–”, it won’t affect your database.
How to Use:
- Make sure you have a MySQL database named “test_db” with a table “users” having columns “id, username, and password”.
- Insert some data into the “users” table to test the script.
- Cross-Site Scripting (XSS) Prevention: XSS attacks are all about injecting malicious scripts into your website. The best defense is to sanitize all user input and output to ensure that only safe data gets through.
- File Upload Security: If you’re allowing file uploads on your site, make sure you’re validating and sanitizing those files. Proper file upload security can prevent attackers from sneaking in malicious code disguised as harmless files.
- Cross-Site Request Forgery (CSRF) Prevention: Cross-Site Request Forgery (CSRF) is an attack where a malicious site tricks the user into submitting a request to another site where they are authenticated, without their consent. To prevent CSRF, tokens are used to verify the legitimacy of the request. Here’s an example of how to implement CSRF prevention in PHP using tokens.Example Code for CSRF Prevention in PHP:
- Generate a CSRF Token and store it in the session when rendering a form.
- Validate the CSRF Token upon form submission.
Step 1: Create a Form with a CSRF Token
//========php========= <?php // Start the session to store the CSRF token session_start(); // Generate a CSRF token if it's not already set if (empty($_SESSION['csrf_token'])) { $_SESSION['csrf_token'] = bin2hex(random_bytes(32)); // Generate a random token } ?> <!-- Sample form with CSRF token embedded --> <form action="process.php" method="POST"> <input type="hidden" name="csrf_token" value="<?php echo $_SESSION['csrf_token']; ?>"> <label for="username">Username:</label> <input type="text" name="username" id="username"> <label for="password">Password:</label> <input type="password" name="password" id="password"> <button type="submit">Submit</button> </form>Step 2: Validate the CSRF Token on Form Submission (“process.php”)
//========php======== <?php session_start(); // Check if the CSRF token exists and matches the session token if ($_SERVER['REQUEST_METHOD'] === 'POST') { if (!empty($_POST['csrf_token']) && hash_equals($_SESSION['csrf_token'], $_POST['csrf_token'])) { // Process the form if the CSRF token is valid $username = $_POST['username']; $password = $_POST['password']; // Do the login or other processing... echo "Form submitted successfully!"; // After successful validation, you can unset the token to avoid reuse unset($_SESSION['csrf_token']); } else { // If the token is invalid, reject the request die("Invalid CSRF token."); } } else { // Invalid request method die("Invalid request."); } ?>Explanation:
- Token Generation: When the form is generated, a unique CSRF token is created using “random_bytes(32)” and stored in the session. The token is also embedded in a hidden form field.
- Token Validation: When the form is submitted, the server compares the token submitted with the form “($_POST[‘csrf_token’])” against the token stored in the session “($_SESSION[‘csrf_token’])” using “hash_equals()” for a safe comparison.
- Secure Submission: If the tokens match, the request is processed. If not, the request is rejected as it might be a CSRF attack.
Important Notes:
- CSRF tokens should be unique and unpredictable for each session or form.
- Always use “hash_equals()” for secure string comparison to prevent timing attacks.
- Ensure you’re using HTTPS for secure token transmission.
3. Implementing Security Header:
Security headers are a powerful tool in your defense arsenal. Here’s how to use them effectively:
- HTTP Strict Transport Security (HSTS): HSTS forces browsers to use HTTPS, which helps protect your site from downgrade attacks. It’s a simple yet effective way to ensure that your site’s communications are always secure.
- Content Security Policy (CSP): CSP is all about controlling what resources can be loaded on your site. By setting a strict content security policy, you can prevent malicious content from being injected into your pages.
- Clickjacking Protection: Clickjacking is a cunning attack that tricks users into clicking something they didn’t intend to. Protect your site by using headers that prevent your content from being embedded in malicious frames.
4. Using Security-Focused Hosting Providers:
Your choice of hosting provider plays a huge role in your site’s security. Here’s what to look for:
- Managed WordPress Hosting: A managed WordPress hosting provider can take a lot of the security burden off your shoulders. These providers specialize in WordPress security and maintenance, so you can focus on your content while they handle the technical details.
- Security Features: Look for hosting providers that offer built-in security features like firewalls, malware scanning, and regular security updates. These features add extra layers of protection, keeping your site safe from threats.
By implementing these advanced security techniques, you’re not just reacting to threats—you’re staying ahead of them. Strengthen your WordPress site’s defenses and keep it secure against whatever comes your way.
WordPress Security Testing and Auditing
When it comes to WordPress security, testing and auditing are crucial steps in maintaining a strong defense. Here’s how to make sure your site stays secure:
1. Regular Security Audits
- Internal Audits: Conducting regular internal audits is key to staying ahead of potential threats. Periodically assess your WordPress setup to identify vulnerabilities and weaknesses before they become serious issues. These audits give you a clear picture of where your site stands and what needs attention.
- External Audits: Sometimes, an outside perspective can uncover what you might miss. Hiring a seasoned WordPress developer to conduct independent audits provides expert recommendations and insights. External audits can be an invaluable part of your security strategy, offering a fresh set of eyes on your site’s defenses.
2. Using Security Scanning Tools
- Automated Tools: Don’t overlook the power of automated security scanning tools. These tools can quickly identify vulnerabilities like SQL injection, cross-site scripting, and weak passwords. They’re a critical part of your security toolkit, helping you catch issues before they’re exploited. Popular examples include Wordfence and Sucuri SiteCheck.
- Vulnerability Databases: Staying informed is half the battle. Subscribe to vulnerability databases and security advisories to keep up with the latest threats and patches. This proactive approach ensures you’re always in the loop and can respond swiftly to emerging risks.
3. Penetration Testing to Identify Vulnerabilities
- Simulated Attacks: Penetration testing takes your security efforts to the next level. By employing professional testers to simulate real-world attacks, you can see how your site holds up under pressure. It’s an effective way to identify weaknesses that might slip through the cracks during regular audits.
- Identify Weaknesses: Penetration tests can reveal vulnerabilities that automated scans might miss. These tests provide a deeper understanding of your site’s security posture, highlighting areas that need immediate attention.
- Prioritize Fixes: Once vulnerabilities are identified, it’s crucial to prioritize fixes. Focus on addressing critical issues uncovered during penetration testing to ensure your site remains secure against the most serious threats.
By combining regular audits, security scanning tools, and penetration testing, you can build a comprehensive understanding of your WordPress site’s security. This approach allows you to proactively address vulnerabilities, keeping your site secure and your users safe.
Additional Security Considerations
As your WordPress site grows and evolves, so do the security challenges. Here are some key areas to focus on:
1. Security for WordPress Multisite
- Centralized Management: WordPress Multisite is a powerful tool, but with great power comes added responsibility. Managing multiple sites from a single dashboard is convenient, but it also means a single vulnerability could impact all your sites. Strengthen security at the network level to protect the entire ecosystem.
- Isolated Sites: To minimize the risk, consider isolating individual sites within your Multisite network. This way, if one site is compromised, the damage doesn’t ripple through to others. Isolation adds a layer of protection that’s worth considering.
- Plugin and Theme Management: Managing plugins and themes across a Multisite network can be tricky. Ensure consistency and security by carefully selecting and regularly updating all plugins and themes. This uniformity helps reduce the risk of vulnerabilities.
2. Security for WooCommerce
- Payment Gateway Security: When it comes to eCommerce, your payment gateway is a critical touchpoint. Always choose reputable payment gateways and strictly follow PCI DSS compliance standards to safeguard your customers’ financial information.
- Data Encryption: Protecting customer data isn’t optional—it’s essential. Use encryption for any sensitive information, such as payment details, to ensure that even if data is intercepted, it remains secure.
- Regular Updates: WooCommerce and its extensions are constantly evolving. Keep everything up to date to address any vulnerabilities that may arise. Staying current with updates is a key part of maintaining a secure eCommerce environment.
3. Security for Headless WordPress
- API Security: Headless WordPress setups rely heavily on APIs, and securing these endpoints is non-negotiable. Implement robust API security measures to protect your backend from unauthorized access and potential breaches.
- Frontend Security: Don’t forget about the security of your frontend applications, especially those that consume the headless WordPress API. Ensure they are as secure as your backend to maintain a comprehensive security posture.
- Data Privacy: With headless setups, user data often flows through various channels. It’s crucial to protect this data and comply with relevant privacy regulations. Implement best practices for data privacy to keep user information safe and your site compliant.
4. Security for WordPress Themes and Plugins
- Theme and Plugin Reviews: Not all themes and plugins are created equal. Choose those from reputable developers who have a track record of quality and security. This reduces the likelihood of introducing vulnerabilities through third-party code.
- Regular Updates: Just like the WordPress core, themes and plugins need regular updates to stay secure. Make it a priority to keep everything up to date, addressing security vulnerabilities as they’re identified.
- Code Quality: Whether you’re using third-party themes and plugins or developing your own, code quality matters. Review the code to identify potential security risks before they become problems.
- Custom Theme and Plugin Development: If you’re developing custom themes or plugins, security best practices should be a cornerstone of your process. This proactive approach ensures that your custom code doesn’t become a weak link in your site’s defenses.
You May Also Read: A Step-by-Step Guide to Build a Headless WordPress Website with React
Conclusion
Securing your WordPress site is essential. Stay proactive, informed, and vigilant. Implement a range of security measures, from basic best practices to advanced techniques. Regularly audit, update, and prioritize quality code. A secure site protects your data, reputation, and user trust. Invest in your site’s security for long-term success.
Stay secure, stay ahead, and keep building with confidence. Need expert help? Contact us for professional security consulting or implementation.