Web Security Best Practices: Protecting Your Website from Attacks
Table of Contents
In today’s digital landscape, web security is more critical than ever. With cyber threats evolving rapidly, it’s essential for website owners and developers to stay ahead of potential vulnerabilities. Whether you’re involved in custom website development or managing an existing site, understanding the latest security best practices is crucial.
This blog post will explore key web security best practices to help protect your website from various attacks, incorporating real-world scenarios and practical advice.
Understanding the Threat Landscape
Before diving into specific practices, let’s look at some sobering statistics that highlight the importance of web security:
- According to IBM’s Cost of a Data Breach Report 2023, the average cost of a data breach reached an all-time high of $4.45 million.
- The same report found that 51% of organizations plan to increase security investments as a result of a breach.
- Cybersecurity Ventures predicts that cybercrime will cost the world $10.5 trillion annually by 2025, up from $3 trillion in 2015.
These numbers underscore the critical need for robust web security measures. Let’s explore some best practices to help safeguard your website, with detailed explanations and real-world applications.
1. Keep Software Up-to-Date
One of the simplest yet most effective security measures is keeping all software up-to-date. This includes:
- Content Management Systems (CMS)
- Plugins and themes
- Server software
- Libraries and frameworks
Regular updates often include security patches for newly discovered vulnerabilities. Neglecting these updates leaves your site exposed to potential attacks.
Real-world application:
In 2021, a critical zero-day vulnerability was discovered in WordPress plugin Fancy Product Designer, installed on over 17,000 sites. Attackers could exploit this to bypass authentication and upload malicious files. Sites that promptly updated the plugin were protected, while those that didn’t were at risk of complete site takeover.
Implementation tips:
- Enable automatic updates where possible
- Set up a regular schedule to check for and apply updates manually
- Use a staging environment to test updates before applying them to your live site
- Keep an inventory of all software and their versions to ensure nothing is overlooked
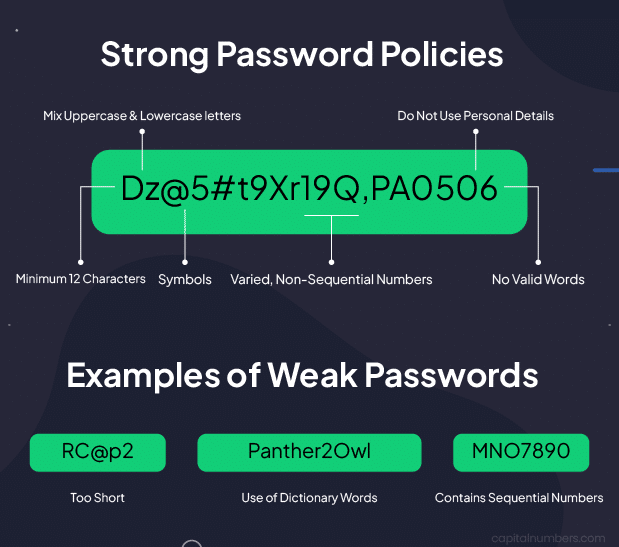
2. Implement Strong Password Policies
Weak passwords remain a common entry point for attackers. Enforce strong password policies by:
- Requiring a minimum length (at least 12 characters)
- Mandating a mix of uppercase and lowercase letters, numbers, and special characters
- Implementing multi-factor authentication (MFA)
- Using a password manager to generate and store complex passwords
Real-world application:
In 2019, Disney+ accounts were hacked within hours of the service’s launch. Many affected users admitted to reusing passwords from other services, highlighting the importance of unique, strong passwords for each account.
Implementation tips:
- Use a reputable password manager like LastPass, 1Password, or Bitwarden
- Implement a password strength meter on registration forms
- Require password changes at regular intervals, but not too frequently to avoid “password fatigue”
- Educate users on the importance of strong, unique passwords
3. Use HTTPS Everywhere
HTTPS (Hypertext Transfer Protocol Secure) encrypts data transmitted between the user’s browser and your website. This protects sensitive information like login credentials and payment details from interception.
To implement HTTPS:
- Obtain an SSL/TLS certificate
- Install the certificate on your web server
- Configure your website to use HTTPS by default
- Use HTTP Strict Transport Security (HSTS) headers
Real-world application:
In 2017, Equifax’s data breach, which exposed sensitive information of 147 million people, was partly due to an expired SSL certificate. This underscores the importance of not just implementing HTTPS, but also maintaining it properly.
Implementation tips:
- Use services like Let’s Encrypt for free SSL certificates
- Implement automatic renewal of SSL certificates to avoid expiration
- Use tools like Qualys SSL Labs to test your SSL implementation
- Configure your web server to redirect all HTTP traffic to HTTPS
4. Implement Web Application Firewalls (WAF)
A Web Application Firewall acts as a shield between your website and the internet, filtering out malicious traffic. WAFs can protect against common attacks such as:
- SQL injection
- Cross-site scripting (XSS)
- Cross-site request forgery (CSRF)
- DDoS attacks
Many cloud providers and CDNs offer WAF services that can be easily integrated into your website’s infrastructure.
Real-world application:
During the 2018 FIFA World Cup, the official website faced numerous cyber attacks. The implementation of a WAF was crucial in mitigating these attacks, allowing the site to handle peak traffic of 4 million requests per second.
Implementation tips:
- Consider cloud-based WAF solutions for easier management and updates
- Regularly update WAF rules to protect against new types of attacks
- Monitor WAF logs to identify and respond to attack patterns
- Use WAF in learning mode initially to avoid false positives before switching to blocking mode
5. Practice Secure Coding Techniques
Developers play a crucial role in website security. Some key secure coding practices include:
- Input validation and sanitization
- Parameterized queries to prevent SQL injection
- Proper error handling and logging
- Implementing Content Security Policy (CSP) headers
- Using secure session management techniques
Regular code reviews and automated security scanning tools can help identify potential vulnerabilities in your codebase.
Real-world application:
In 2017, Uber disclosed a data breach that exposed data of 57 million users. The breach was possible due to hardcoded credentials in the source code, which allowed attackers to access Uber’s GitHub repository and subsequently, their AWS servers.
Implementation tips:
- Use static code analysis tools like SonarQube or Veracode
- Implement peer code reviews with a focus on security
- Follow the OWASP Secure Coding Practices checklist
- Regularly train developers on the latest secure coding techniques
6. Backup Regularly and Securely
While not a direct defense against attacks, regular backups are crucial for recovery in case of a successful breach. Ensure that:
- Backups are performed frequently (daily for dynamic sites)
- Backup files are encrypted
- Backups are stored in a separate, secure location
- You regularly test the restore process to ensure backups are viable
Real-world application:
In 2019, hosting provider A2 Hosting suffered a ransomware attack that took down Windows hosting servers. Clients with recent, secure backups were able to restore their sites quickly, while others faced prolonged downtime.
Implementation tips:
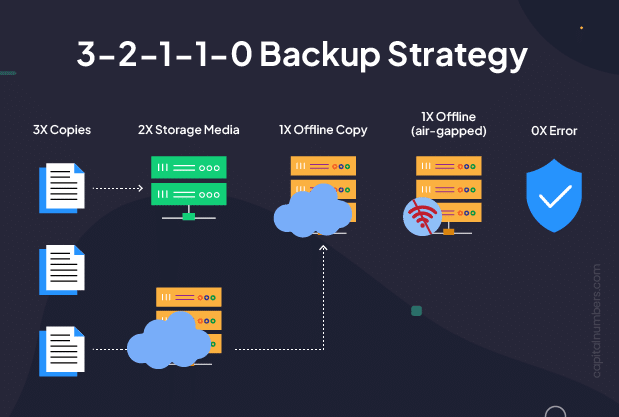
- Implement the 3-2-1 backup strategy: 3 copies of data, on 2 different media, with 1 copy offsite
- Use automated backup solutions to ensure consistency
- Encrypt backups both in transit and at rest
- Regularly perform restore drills to ensure backup integrity
7. Monitor and Log Activity
Implementing robust logging and monitoring systems can help you detect and respond to security incidents quickly. Key areas to monitor include:
- Failed login attempts
- File system changes
- Database queries
- Network traffic patterns
Use tools like intrusion detection systems (IDS) and security information and event management (SIEM) solutions to aggregate and analyze logs effectively.
Real-world application:
The 2013 Target data breach, which exposed 40 million credit card numbers, could have been mitigated if the company had properly monitored and responded to security alerts. Their systems detected the malicious activity, but the alerts were not acted upon.
Implementation tips:
- Centralize logs using tools like ELK stack (Elasticsearch, Logstash, Kibana) or Splunk
- Set up alerts for suspicious activities
- Regularly review and analyze logs for patterns or anomalies
- Ensure logs are stored securely and cannot be tampered with
8. Educate Your Team
Human error remains one of the biggest security risks. Regular training sessions for your team can help mitigate this risk. Cover topics such as:
- Recognizing phishing attempts
- Safe browsing practices
- The importance of updating software
- How to handle sensitive data
Real-world application:
In 2020, Twitter suffered a major breach where high-profile accounts were compromised. The attack was successful due to a social engineering attack on Twitter employees, highlighting the importance of staff education in cybersecurity.
Implementation tips:
- Conduct regular security awareness training sessions
- Use simulated phishing campaigns to test and educate employees
- Create and enforce clear security policies and procedures
- Foster a culture of security awareness within the organization
You May Also Read: WordPress Security: Advanced Techniques and Best Practices
A Personal Experience: Learning the Hard Way
While I don’t have personal experiences, let me share a hypothetical scenario that illustrates the importance of these security practices:
- As a junior developer at a small e-commerce startup, I was tasked with building our company’s first website. Excited about the features and design, I rushed through the development, neglecting many of the security practices mentioned above.
- Two months after launch, disaster struck. We woke up one morning to find our site defaced, customer data stolen, and our reputation in tatters. The attack exploited several vulnerabilities:
- We had used an outdated version of our CMS, which had a known vulnerability.
- Our admin password was weak and easily guessed.
- We hadn’t implemented HTTPS, allowing attackers to intercept login credentials.
- Our backups were irregular and not properly secured.
- The aftermath was devastating. We spent weeks rebuilding the site, dealing with angry customers, and trying to salvage our reputation. The financial cost was significant, but the loss of trust was even more damaging.
- This experience taught me the hard way that security isn’t an afterthought—it’s a fundamental aspect of web development. Since then, I’ve made it my mission to prioritize security in every project, following the best practices outlined in this post.
You May Also Read: Don’t Get Hacked: Essential Software Security Checklist for Developers
Conclusion
Web security is an ongoing process, not a one-time task. By implementing these best practices and staying informed about emerging threats, you can significantly reduce the risk of your website falling victim to cyber attacks.
Remember, the cost of prevention is always lower than the cost of recovery from a successful attack. Invest in your website’s security today to protect your business and your users’ trust tomorrow.
As the threat landscape continues to evolve, so too must our security practices. Stay vigilant, keep learning, and never assume your website is “secure enough.” In the world of web security, complacency is the enemy of safety.
Don’t wait for a breach to happen – take action now to fortify your website’s security. Contact us today to learn how we can help you safeguard your online presence.