12 Best Practices to Secure Your API in the AWS Cloud
Table of Contents
Application Programming Interfaces (APIs) have become the backbone of modern software development in today’s linked digital environment. They allow for the seamless interchange of data and functionality between systems, promoting innovation and improving user experiences. Amazon Web Services (AWS) has evolved as a key platform for hosting and administering APIs, providing a robust and scalable environment for designing and deploying APIs since the dawn of cloud computing. However, greater connectivity comes with increased security vulnerabilities, making API security a top priority for software solutions companies.
Introduction to API Security
API security is important in API development to build and maintain secure and reliable applications. It prevents unauthorized access, data breaches, and other security dangers to your Application Programming Interfaces. Because APIs frequently links between different software components, protecting them is crucial for avoiding vulnerabilities that might disclose sensitive data or interrupt operations.
The Importance of API Security
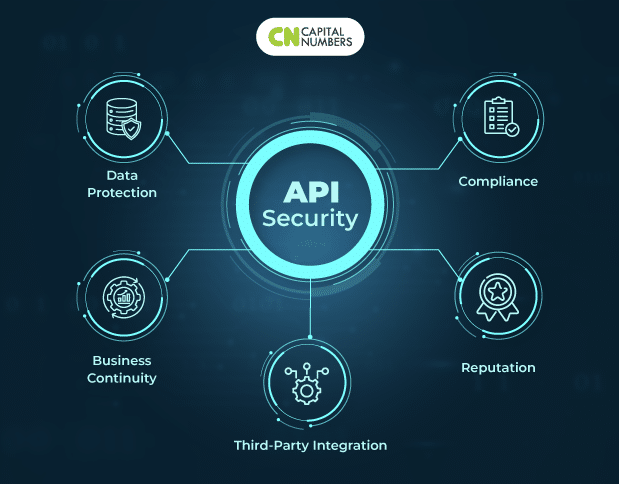
• Data Protection: Safeguarding sensitive data is at the heart of the issue. APIs are used to communicate a wide range of sensitive information, including user passwords, personal data, financial records, and more. In this setting, a security breach might signal disaster, with unthinkable consequences such as data theft, identity fraud, financial losses, and permanent reputational harm. Thus, data security is no longer a luxury in the digital era but an important need.
• Business Continuity: Aside from data security, the integrity of APIs directly impacts business continuity. Unsecured APIs are an open invitation to hostile actors that wish to disrupt systems or cause systemic breakdowns. Such interruptions may be disastrous, resulting in lengthy downtimes, revenue losses, and, as a result, a loss of confidence among customers, partners, and stakeholders.
• Compliance: Adherence to regulatory compliance is required in an era of increasing emphasis on data privacy and security. The General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) are two examples of strict laws that several businesses and geographical locations have enacted. These standards require stringent data security practices and levy harsh fines for noncompliance. As a result, insufficient API security jeopardizes data and exposes organizations to significant legal and financial implications.
• Reputation: API security is critical for brand image maintenance in the digital environment, where reputation and trust are valuable assets. A security breach may irreversibly harm a brand’s reputation and destroy customer confidence. Rebuilding damaged trust is sometimes a mammoth task with long-term ramifications.
• Third-Party Integration: APIs are rarely used in isolation. They regularly interface with systems and services provided by third parties. The security of your APIs directly impacts the security posture of these linked systems. An unsecured API can cause a chain reaction, resulting in vulnerabilities and potential breaches throughout a linked network of digital processes.
API Security Best Practices
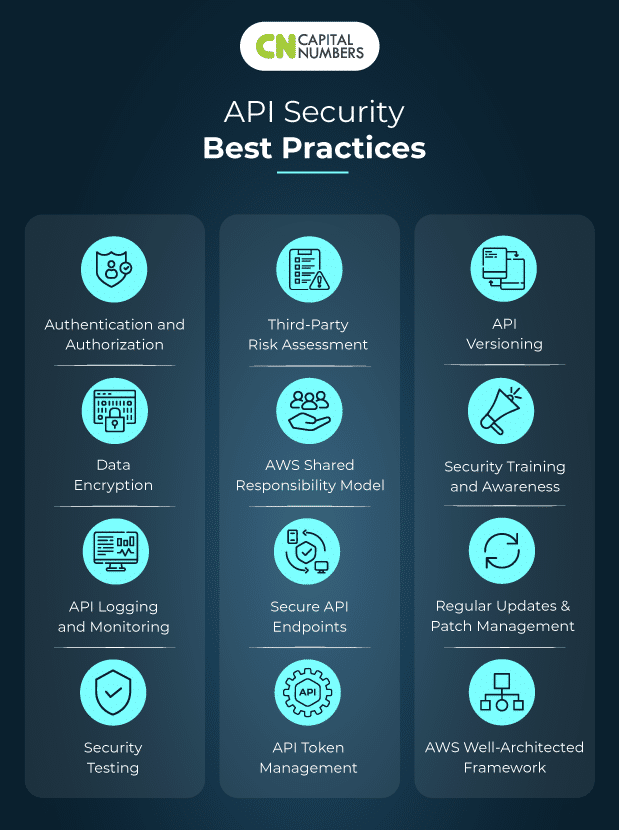
AWS experts focus on API security to prevent data breaches, ensure compliance, safeguard AWS resources against unauthorized access, and more. Following are the full API security best practices recommended by Capital Numbers, with an emphasis on AWS:
1. Authentication and Authorization
- Authentication verifies the identity of users or systems trying to access the API, while authorization determines the level of access granted to authenticated entities.
- Employ industry-standard authentication methods like OAuth2, JWT (JSON Web Tokens), or API keys.
- Leverage AWS Identity and Access Management (IAM) to manage access to AWS resources securely. Ensure that IAM policies are well-defined and limited to the minimum required permissions.
- Assign specific roles and permissions to users or systems to ensure they can only access authorized resources.
2. Secure API Endpoints
- API endpoints are the entry points to your system. Securing them is a fundamental step in API security.
- Validate and sanitize user input to prevent common vulnerabilities like SQL injection and Cross-Site Scripting (XSS).
- Amazon API Gateway is a critical component for managing and securing APIs. Configure it to handle authentication, request validation, and rate limiting.
- Utilize AWS API Gateway’s request validation features to define and enforce input validation rules, ensuring that only well-formed, safe requests reach your backend.
- Implement rate limiting using AWS API Gateway’s built-in features to prevent abuse and brute-force attacks.
3. Data Encryption
- Encrypting data in transit and at rest protects sensitive information from interception or theft.
- Use HTTPS to encrypt data in transit and ensure that your SSL/TLS certificates are up-to-date.
- Use AWS Certificate Manager (ACM) to manage SSL/TLS certificates for your AWS APIs.
- Employ encryption mechanisms to protect data at rest or stored in databases or on disk. Utilize AWS services like Amazon S3, Amazon RDS, or AWS Key Management Service (KMS) to encrypt data at rest.
- Use AWS Key Management Service (KMS) to manage encryption keys and define fine-grained access controls for data encryption.
4. API Token Management
- Managing API tokens, such as API keys or access tokens, is crucial to preventing unauthorized access.
- Regularly rotate API tokens to limit exposure in the event of compromise. Leverage Amazon API Gateway API keys for authentication and restrict access based on API keys.
- Use AWS API Gateway API keys to control access to your APIs and set up usage plans to manage rate limits and quotas.
5. API Logging and Monitoring
- Comprehensive logging and real-time monitoring help detect and respond to security incidents.
- Maintain detailed logs of API activities to track suspicious behavior. Enable AWS CloudTrail to capture API calls and monitor AWS resource changes.
- Implement SIEM solutions to monitor and analyze API logs for anomalies. Set up Amazon CloudWatch alarms to trigger notifications for suspicious activities.
- Create CloudWatch dashboards and alarms to gain insights into the performance and security of your AWS APIs.
6. API Versioning
- Maintain backward compatibility while evolving your APIs to ensure existing integrations remain secure.
- Use versioning schemes like Semantic Versioning (SemVer) to clearly communicate changes and ensure smooth upgrades.
7. Security Testing
- Regularly test your APIs for vulnerabilities using tools like penetration testing and security scanning.
- Conduct regular penetration tests to identify weaknesses in your API security. Utilize AWS Inspector to assess the security of your AWS resources and APIs.
- Employ static and dynamic analysis tools to scan code for vulnerabilities. Consider using third-party vulnerability scanning tools that integrate seamlessly with AWS.
- Leverage AWS Inspector to automate security assessment tasks, including vulnerability scanning and compliance checks.
8. Security Training and Awareness
- Educate your development and operations teams about API security best practices.
- Provide training on secure coding practices and common security threats. Take advantage of AWS training resources and certifications to ensure your team is well-versed in AWS security.
- Develop and regularly update an incident response plan to address security breaches promptly. Create a specific incident response plan for AWS to handle security incidents within the AWS Cloud.
9. Third-Party Risk Assessment
- Assess the security practices of third-party APIs your system interacts with.
- Evaluate the security controls and practices of third-party API providers before integration.
10. Regular Updates and Patch Management
- Keep your API frameworks, libraries, and dependencies up-to-date to mitigate known vulnerabilities.
- Monitor security advisories and apply patches promptly to address known vulnerabilities.
11. AWS Shared Responsibility Model
- Understand the AWS Shared Responsibility Model, which defines the division of security responsibilities between AWS and the customer.
- Be aware of your responsibilities for securing data and configurations within AWS services.
12. AWS Well-Architected Framework
- Follow the AWS Well-Architected Framework’s security best practices to design and operate secure and resilient workloads.
- Pay particular attention to the Security Pillar of the AWS Well-Architected Framework, which guides on implementing security best practices.
Also Read : What Is Serverless Computing?
Conclusion
API security within the AWS ecosystem is critical to modern cloud computing. Capital Numbers, a credible software solutions company, recognizes the importance of safeguarding your data in the age of interconnected systems and APIs hosted on AWS. By following these comprehensive API security best practices specifically tailored for the AWS ecosystem, you can significantly reduce the risk of security breaches, protect your data, and maintain the trust of your customers and partners. Remember that API security is not a one-time effort but an ongoing commitment to stay ahead of evolving digital and cloud computing threats. Stay vigilant, informed, and proactive in securing your APIs in the AWS cloud.