Optimizing API Performance and Security: The Essential Guide
Table of Contents
Application Programming Interfaces (APIs) are crucial for the smooth interaction between different software and internet services, acting as the foundation for many digital operations. With the increasing dependency on APIs, the challenges of keeping them performing well and secure are also on the rise. This is where the expertise of API development companies comes into play. These companies specialize in navigating the complexities of API optimization, ensuring that applications not only perform optimally but are also safeguarded against the latest cyber threats.
This guide explores vital strategies and practices for improving the efficiency and security of your APIs. It’s packed with valuable insights and actionable advice, catering to both experienced developers and those new to the field. You’ll learn how to navigate the complexities of API optimization effectively, ensuring your applications not only perform optimally but are also safeguarded against the latest cyber threats.
Let’s explore ways to improve the speed and safety of your APIs.
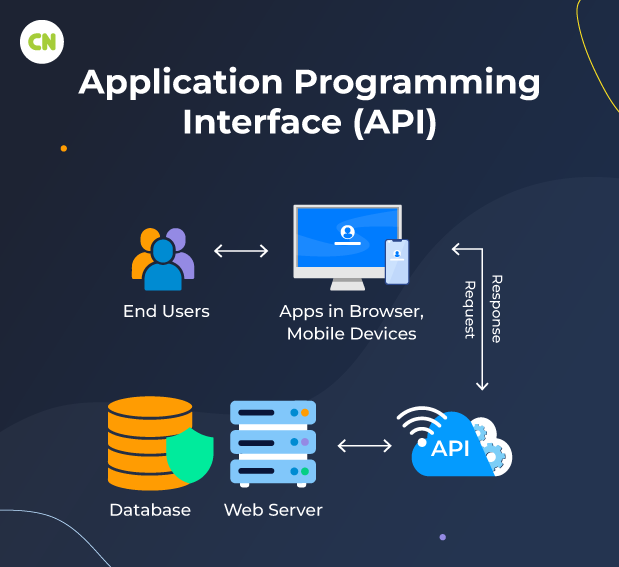
What is an API?
SOAP API and REST API
SOAP (Simple Object Access Protocol) API and REST (Representational State Transfer) API are two common types of Application Programming Interfaces used to facilitate communication and interaction between software systems. SOAP API, based on XML, defines a strict protocol for exchanging structured information over a network. It relies on the XML messaging format for sending and receiving requests and responses, often using HTTP or other protocols for transport. In contrast, REST API, based on the principles of the web, utilizes a more lightweight and flexible approach to data exchange.
REST APIs typically use standard HTTP methods like GET, POST, PUT, and DELETE to perform operations on resources identified by URIs. Unlike SOAP, REST APIs commonly employ JSON or XML as the data interchange format, offering greater simplicity and compatibility with modern web technologies. SOAP and REST APIs have advantages and use cases, with SOAP being favored for its strict standards and advanced features like security and reliability. At the same time, REST is preferred for its simplicity, scalability, and ease of use in web-based applications.
You May Also Read : API Development FAQs: Get Your Questions Answered and Start Building
Optimizing API Performance
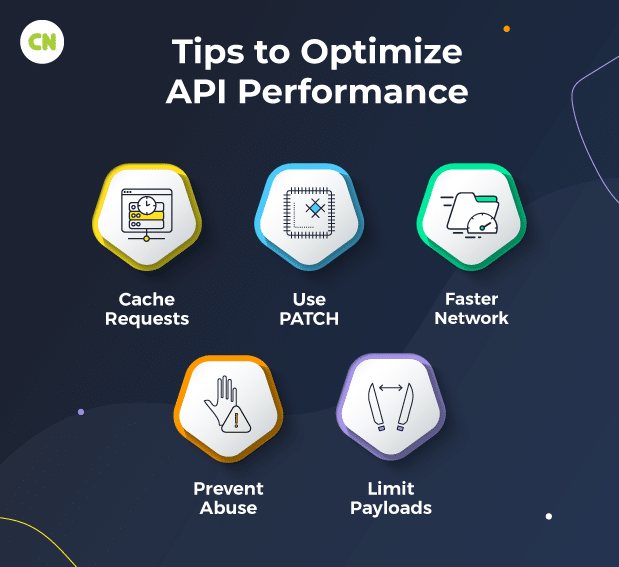
Cache Requests
API optimization through cache requests involves implementing mechanisms to store and reuse frequently accessed responses, enhancing performance and reducing latency. This process revolves around leveraging the principle of caching, where responses from previous requests are stored temporarily and served to subsequent requests without recomputing or retrieving data from the original source. By doing so, cache requests minimize the computational overhead and network latency associated with processing redundant queries or data retrieval operations.
The implementation of cache requests typically involves several key steps. Firstly, developers identify the portions of the API response suitable for caching based on factors such as frequency of access, data volatility, and computational intensity. For example, static data or data that changes infrequently, such as reference data or configuration settings, are prime candidates for caching. Conversely, dynamic data subject to frequent updates or user-specific customization may be less suitable for caching.
Once the cacheable data is identified, developers configure the caching strategy, which includes determining the caching duration or expiration policy. This policy dictates how long the cached responses remain valid before they are considered stale and need to be refreshed. For instance, data that rarely changes may have a longer caching duration, whereas volatile data may require more frequent updates to ensure freshness.
Moreover, cache invalidation mechanisms are implemented to manage the lifecycle of cached data and ensure that clients receive the most up-to-date information when necessary. This involves establishing triggers or events that signal when cached data should be invalidated or refreshed, such as data updates, changes in system state, or expiration of predefined time intervals.
From a technical standpoint, cache requests are often implemented using dedicated caching solutions or frameworks, such as in-memory caches like Redis or distributed caching systems like Hazelcast or Apache Ignite. These systems provide efficient storage and retrieval of cached data and features such as expiration policies, cache eviction strategies, and distributed coordination for scalability and fault tolerance.
Optimizing APIs with cache requests offers several benefits, including improved response times, reduced server load, enhanced scalability, and better overall user experience. By intelligently caching frequently accessed data, organizations can streamline API performance, mitigate latency issues, and achieve higher application efficiency and responsiveness.
Prevent Abuse
API optimization through the prevention of abuse involves implementing strategies to mitigate the risks associated with malicious or unintentional misuse of the API, thereby safeguarding system resources, maintaining stability, and ensuring fair access for legitimate users. This process revolves around rate limiting and access control, which aim to monitor and manage the volume and frequency of requests made to the API.
The first step in preventing abuse is to implement rate-limiting mechanisms, which involve setting thresholds or quotas on the number of requests that can be made within a specific period. This prevents individual users or applications from overwhelming the API with excessive requests, leading to performance degradation or denial of service for other users. Rate limiting can be applied at various levels, such as per IP address, user account, API key, or client application, depending on the desired granularity of control.
Access control measures are also implemented to authenticate and authorize users or applications before granting them access to API resources. This involves verifying the identity of users through authentication mechanisms like API keys, OAuth tokens, or user credentials and enforcing access permissions based on predefined roles or policies. Access control helps prevent unauthorized access to sensitive data or operations, reducing the risk of data breaches or unauthorized activities.
Use PATCH
API optimization through the utilization of the PATCH method involves enhancing performance and efficiency by selectively updating resources with partial modifications. Unlike the PUT method, which replaces the entire resource with the updated version, PATCH allows clients to make incremental changes to specific attributes or fields within a resource. This granularity in updates minimizes the payload size and reduces the amount of data transmitted over the network, leading to improved performance and bandwidth utilization.
The implementation of PATCH optimization typically involves several key considerations. Firstly, developers identify the portions of the resource that require modification and determine the corresponding patch operations to be applied. Depending on the desired changes, these operations may include adding, updating, or removing specific attributes within the resource.
Once the patch operations are defined, developers implement the PATCH request handler on the server side to process incoming requests and apply the specified changes to the resource. This involves parsing the patch document provided by the client, interpreting the patch operations, and using them to the resource’s current state. Careful attention is paid to handling concurrency and ensuring data consistency during the patch operation, especially when multiple clients attempt to update the same resource concurrently.
From a client perspective, optimizing API usage with PATCH involves crafting efficient patch documents that encapsulate only the necessary changes to the resource. Clients should avoid sending redundant or unnecessary data in the patch request, focusing instead on transmitting only the modified attributes or fields. This minimizes the payload size and reduces network overhead, resulting in faster request processing and improved overall performance.
Limit Payloads
API optimization with limited payloads focuses on reducing the size of data payloads exchanged between clients and servers, thereby improving performance and efficiency. This optimization strategy is particularly relevant for APIs that handle large volumes of data or are accessed by devices with limited bandwidth or processing capabilities. By minimizing the amount of data transferred over the network, limit payloads help to reduce latency, conserve bandwidth, and enhance overall responsiveness.
To implement limit payloads effectively, developers employ various techniques and best practices:
- Compression: One of the primary methods for reducing payload size is data compression. By compressing data before transmission and decompressing it upon receipt, APIs can significantly reduce the amount of bandwidth required for data exchange. Popular compression algorithms such as gzip are commonly used to compress textual data formats like JSON or XML, resulting in substantial reductions in payload size without sacrificing data integrity.
- Selective Data Transmission: APIs can optimize payloads by selectively transmitting only the data that is required by the client. Instead of sending entire datasets or resource representations, APIs tailor responses to include only the necessary fields or attributes requested by the client. This approach, often referred to as partial response or field selection, minimizes payload size by excluding extraneous data, thereby reducing network overhead and improving performance.
- Pagination: For APIs that return large datasets or collections of resources, pagination is a useful technique for limiting payload size. Rather than returning all records in a single response, APIs paginate results by breaking them into smaller chunks or pages. Clients can then request subsequent pages of data as needed, enabling efficient retrieval of large datasets while maintaining manageable payload sizes.Pagination reduces the risk of performance degradation and network congestion associated with transmitting excessively large responses in a single request.
- Data Compression: Another effective approach to limit payloads is by compressing the data being transmitted. Techniques such as data compression algorithms like GZIP can significantly reduce the size of data payloads, resulting in faster transmission times and reduced bandwidth usage. By compressing data before sending it over the network and decompressing it upon receipt, APIs can optimize performance and enhance the efficiency of data exchange processes.
- Client-Side Filtering: APIs can delegate some of the payload reduction responsibilities to the client by offering filtering capabilities. Clients can specify criteria or parameters to filter the data returned by the API, ensuring that only relevant information is transmitted. By enabling client-side filtering, APIs empower clients to customize their data requests according to their specific needs, resulting in leaner payloads and improved performance.
Faster Network
API optimization through a faster network involves enhancing the infrastructure and network configuration to minimize latency, increase throughput, and improve the overall performance of API communication. A faster network contributes significantly to reducing response times, enhancing user experiences, and ensuring the reliability and responsiveness of APIs. This optimization strategy encompasses several key aspects aimed at optimizing network connectivity, improving data transmission efficiency, and mitigating network-related bottlenecks. Firstly, investing in high-quality network infrastructure and reliable hosting services is essential for ensuring optimal API performance. Organizations should leverage reputable cloud service providers or data centers with robust network connectivity, low latency, and high availability. By selecting hosting environments with strategically located servers and redundant network architecture, organizations can minimize latency and ensure consistent access to APIs from diverse geographic regions.
Moreover, optimizing network connections involves implementing techniques to reduce packet loss, optimize routing paths, and enhance connection reliability. This may include configuring network devices, such as routers and switches, to prioritize API traffic, minimize network congestion, and optimize data transmission paths. Additionally, leveraging content delivery networks (CDNs) or edge computing solutions can help distribute API endpoints closer to end-users, reducing latency and improving response times for geographically distributed clients.
To address performance issues related to background tasks or long-running operations, organizations should adopt strategies to isolate and prioritize API traffic from other network activities. This may involve running background tasks on separate threads or processes to avoid blocking API requests and ensure timely response delivery. Additionally, implementing asynchronous communication patterns, such as message queues or event-driven architectures, can help decouple API interactions from resource-intensive background processes, improving overall system responsiveness.
You May Also Read : 7 Game-Changing Tips to 10x Your API Performance
API Security Threats
API security threats pose significant risks to the confidentiality, integrity, and availability of data exchanged through APIs. These threats encompass a wide range of attack vectors and vulnerabilities that malicious actors may exploit to compromise API endpoints, gain unauthorized access to sensitive information, or disrupt API operations. Understanding and mitigating these threats is crucial for safeguarding API ecosystems and maintaining the trust of users and stakeholders. Here are some common API security threats:
- Injection Attacks: Injection flaws, such as SQL injection and command injection, occur when attackers manipulate input data to execute malicious commands or queries against the underlying systems. This can lead to unauthorized data access, data manipulation, or even complete system compromise.
- Broken Authentication: Broken authentication vulnerabilities allow attackers to bypass authentication mechanisms or compromise user credentials, enabling unauthorized access to API endpoints or sensitive data. Weak password policies, session management flaws, or improper implementation of authentication mechanisms contribute to this threat.
- Sensitive Data Exposure: APIs may inadvertently expose sensitive data, such as personally identifiable information (PII) or financial data, due to inadequate access controls, improper data handling, or insufficient encryption. Attackers exploit this vulnerability to steal confidential information or conduct identity theft.
- Broken Access Controls: Broken access control vulnerabilities occur when APIs fail to enforce proper authorization checks, allowing unauthorized users to access restricted resources or perform privileged actions. This can result in data leakage, privilege escalation, or unauthorized data modification.
- Security Misconfigurations: Security misconfigurations, such as default settings, weak encryption algorithms, or improper error handling, create opportunities for attackers to exploit vulnerabilities and gain unauthorized access to API endpoints or sensitive data. Regular security audits and proper configuration management are essential to mitigate this threat.
- Denial of Service (DoS) Attacks: DoS attacks target API endpoints with a flood of malicious requests, overwhelming the server infrastructure and causing service disruptions or downtime. This can result in loss of availability, degraded performance, or financial losses for organizations.
- Insufficient Logging and Monitoring: Inadequate logging and monitoring practices make it difficult to detect and respond to security incidents, such as unauthorized access attempts or data breaches. Without proper visibility into API activities, organizations may fail to identify and mitigate security threats in a timely manner.
- API Abuse and Rate Limiting Bypass: Malicious actors may abuse APIs by sending excessive requests or exploiting rate limiting mechanisms to bypass access controls and overwhelm the server infrastructure. Implementing effective rate limiting, throttling, and bot detection mechanisms is essential to mitigate this threat.
- Man-in-the-Middle (MitM) Attacks: MitM attacks intercept and manipulate communication between clients and API endpoints, enabling attackers to eavesdrop on sensitive data, modify requests or responses, or impersonate legitimate users. Encrypting API traffic with secure protocols, such as HTTPS/TLS, helps mitigate this risk.
- Insecure APIs and Libraries: Insecure APIs or third-party libraries may contain vulnerabilities or weaknesses that attackers can exploit to compromise API endpoints or inject malicious code into applications. Regular security assessments, code reviews, and dependency scanning are essential to identify and remediate security flaws in APIs and libraries.
Broken Object-Level Authorization
Broken Object-Level Authorization (BOLA), also known as Insecure Direct Object References (IDOR), is a critical API security vulnerability that occurs when an API fails to properly enforce authorization controls at the object level, allowing attackers to access unauthorized resources or manipulate sensitive data.
This vulnerability arises when APIs expose direct references to internal objects, such as database records or file paths, in their request parameters or URLs. Attackers can exploit these direct object references by tampering with identifiers or parameters in API requests to gain unauthorized access to sensitive resources or manipulate data associated with other users.
For example, consider an API endpoint that retrieves user data based on a user ID supplied in the request. If the API does not validate the user’s permissions or ownership of the requested data, attackers can modify the user ID parameter to access sensitive information belonging to other users. This could result in unauthorized access to personal information, financial records, or other confidential data, leading to privacy breaches or identity theft.
To mitigate Broken Object-Level Authorization vulnerabilities, organizations should implement robust authorization mechanisms that enforce access controls at the object level. This involves validating user permissions and ownership rights for each requested resource, rather than relying solely on client-supplied identifiers or parameters.
Key strategies for addressing BOLA vulnerabilities include:
- Contextual Authorization: Implement context-aware authorization mechanisms that consider the user’s role, privileges, and relationship to the requested resource. This ensures that users can only access or manipulate objects that they are authorized to interact with.
- Indirect Object References: Avoid exposing direct references to internal objects in API responses or URLs. Instead, use indirect references or surrogate keys that cannot be easily manipulated by attackers to access unauthorized resources.
- Access Control Checks: Perform access control checks at multiple layers of the application stack, including API endpoints, business logic components, and data access layers. This helps prevent unauthorized access to sensitive data at various levels of the application architecture.
- Secure Authentication: Ensure secure authentication mechanisms are in place to authenticate users and verify their identities before granting access to sensitive resources. Use strong authentication factors, such as multi-factor authentication (MFA), to enhance security.
- Input Validation: Validate and sanitize input parameters and user-supplied data to prevent injection attacks, such as parameter tampering or SQL injection, that could be used to exploit BOLA vulnerabilities.
- Role-Based Access Control (RBAC): Implement RBAC policies that define roles, permissions, and access levels for different user groups. Enforce these policies consistently across all API endpoints to limit access to authorized users only.
- Audit Trails and Logging: Maintain comprehensive audit trails and logging mechanisms to track user activities, API access attempts, and data modifications. Regularly review audit logs to detect and investigate suspicious behavior or unauthorized access attempts.
Broken User Authentication
Broken User Authentication is a critical API security vulnerability that occurs when authentication mechanisms are improperly implemented or compromised, allowing attackers to bypass authentication controls and gain unauthorized access to protected resources or sensitive data. This vulnerability undermines the confidentiality, integrity, and availability of API endpoints, potentially leading to data breaches, identity theft, and unauthorized system access.
This vulnerability arises from various weaknesses in authentication mechanisms, including:
Weak Password Policies: Insecure password policies, such as allowing weak or easily guessable passwords, not enforcing password complexity requirements, or failing to implement password expiration policies, weaken user authentication and increase the risk of brute-force attacks or credential stuffing.
Insecure Authentication Protocols: The use of outdated or insecure authentication protocols, such as Basic Authentication or HTTP Digest Authentication without encryption, exposes credentials to interception or replay attacks. Secure protocols like OAuth 2.0 or OpenID Connect should be used to protect sensitive data during authentication.
Session Management Flaws: Poorly managed user sessions, such as session fixation, session hijacking, or insufficient session expiration controls, allow attackers to exploit authenticated sessions to impersonate legitimate users or access unauthorized resources. Secure session management practices, including unique session identifiers, session expiration timeouts, and secure session storage, mitigate these risks.
Insufficient Credential Protection: Failure to adequately protect user credentials, such as storing passwords in plaintext, using weak cryptographic hashing algorithms, or exposing sensitive authentication tokens in cleartext, enables attackers to compromise user accounts and gain unauthorized access to API endpoints. Strong encryption, secure password hashing algorithms (e.g., bcrypt, Argon2), and secure credential storage mechanisms should be employed to safeguard user credentials.
Missing Multi-Factor Authentication (MFA)
Lack of multi-factor authentication (MFA) increases the risk of account compromise by relying solely on single-factor authentication mechanisms (e.g., passwords). Implementing MFA, such as SMS codes, hardware tokens, or biometric authentication, strengthens user authentication and mitigates the impact of compromised credentials.
To mitigate Broken User Authentication vulnerabilities, organizations should implement robust authentication controls and best practices, including:
- Secure Password Policies: Enforce strong password policies, including minimum length requirements, complexity rules, and regular password rotation, to prevent weak or easily guessable passwords.
- Secure Authentication Protocols: Use secure authentication protocols, such as OAuth 2.0 or OpenID Connect, with strong encryption and protection against common attacks like man-in-the-middle (MitM) and replay attacks.
- Session Management Controls: Implement secure session management practices, such as unique session identifiers, session expiration timeouts, and secure session storage mechanisms, to prevent session-related vulnerabilities.
- Secure Credential Storage: Store user credentials securely using industry-standard cryptographic hashing algorithms (e.g., bcrypt, Argon2) with salted hashes to protect against password cracking and credential theft.
- Multi-Factor Authentication (MFA): Enable multi-factor authentication (MFA) to add an additional layer of security beyond passwords, requiring users to verify their identity using multiple factors before accessing sensitive resources.
- Regular Security Audits: Conduct regular security audits and penetration testing to identify and remediate vulnerabilities in authentication mechanisms, ensuring compliance with security best practices and standards.
Excessive Data Exposure
Excessive Data Exposure in API security refers to the inadvertent or unauthorized disclosure of sensitive or unnecessary data through API endpoints, exposing organizations to significant privacy and compliance risks. This vulnerability occurs when APIs return more data than required or expose sensitive information to unauthorized users, potentially leading to data breaches, identity theft, or regulatory violations.
There are several factors that contribute to Excessive Data Exposure in APIs:
- Overly Permissive Access Controls: APIs may lack proper access controls or authorization mechanisms, allowing users to access and retrieve more data than necessary. Inadequate validation of user permissions or failure to enforce least privilege principles can result in the exposure of sensitive information to unauthorized users.
- Inadequate Data Filtering and Redaction: APIs may fail to properly filter or redact sensitive data from responses, leading to the unintentional disclosure of confidential information. Without adequate data masking or anonymization techniques, APIs may expose personally identifiable information (PII), financial records, or other sensitive data to unintended recipients.
- Insecure Data Transmission: APIs may transmit sensitive data over unencrypted channels or lack proper encryption mechanisms, exposing data to interception or eavesdropping attacks. Insecure communication protocols, such as HTTP without SSL/TLS encryption, compromise the confidentiality of data in transit and increase the risk of data exposure.
- Insufficient Input Validation: APIs may not perform sufficient input validation or sanitization of user-supplied data, allowing attackers to inject malicious payloads or exploit input-based vulnerabilities (e.g., injection attacks). Failure to validate and sanitize input data increases the likelihood of data exposure through API responses or interactions.
Excessive Data Retention
APIs may retain more data than necessary for legitimate business purposes, increasing the risk of data exposure in the event of a security breach or unauthorized access. Inadequate data retention policies or failure to securely delete obsolete data expose organizations to regulatory non-compliance and data leakage risks.
To mitigate Excessive Data Exposure in APIs, organizations should implement the following security best practices:
- Data Minimization: Limit the amount of data exposed through API responses to only the information necessary for fulfilling legitimate business requirements. Adopt a principle of data minimization to reduce the risk of exposing sensitive information unnecessarily.
- Data Masking and Redaction: Implement data masking or redaction techniques to conceal sensitive information from API responses, such as replacing PII with pseudonymized values or masking financial data. Ensure that only authorized users have access to unmasked data as needed.
- Encryption of Data in Transit and at Rest: Encrypt sensitive data both in transit and at rest using strong encryption algorithms and protocols (e.g., SSL/TLS for data in transit, AES encryption for data at rest). Employ proper key management practices to safeguard encryption keys.
- Input Validation and Sanitization: Implement strict input validation and sanitization mechanisms to prevent injection attacks, cross-site scripting (XSS), and other input-based vulnerabilities. Validate and sanitize all user-supplied data before processing or returning it in API responses.
- Access Controls and Authorization: Enforce robust access controls and authorization mechanisms to restrict access to sensitive data based on user permissions and roles. Implement fine-grained access controls to ensure that users only have access to the data they are authorized to retrieve.
- Regular Security Audits and Testing: Conduct regular security audits, penetration testing, and vulnerability assessments to identify and remediate vulnerabilities related to Excessive Data Exposure. Test APIs for data exposure vulnerabilities using security testing tools and techniques.
Lack of Resource and Rate Limiting
The lack of resource and rate limiting in API security poses a significant risk, potentially leading to denial of service (DoS) attacks, service degradation, or abuse of API resources. This vulnerability arises when APIs do not enforce controls on the number of requests that can be made within a given time period or fail to allocate sufficient resources to handle incoming requests efficiently.
Without adequate resource and rate limiting measures in place, APIs are vulnerable to various security threats, including:
- Denial of Service (DoS) Attacks: Attackers can exploit the absence of rate limiting to flood API endpoints with a high volume of requests, overwhelming server resources and causing service disruptions or downtime. DoS attacks can lead to loss of availability, degraded performance, and financial losses for organizations.
- API Abuse and Misuse: Lack of rate limiting enables malicious actors to abuse API endpoints by sending excessive requests or conducting automated attacks, such as scraping or brute-force attacks, to extract sensitive data or disrupt API operations. This can lead to data breaches, unauthorized access, or exploitation of API vulnerabilities.
Resource Exhaustion
Inadequate resource management and failure to enforce resource limits may result in resource exhaustion, where excessive demands on server resources, such as CPU, memory, or network bandwidth, degrade system performance or cause service interruptions. This can impact the responsiveness and reliability of API endpoints, affecting user experience and business operations.
To mitigate the risks associated with the lack of resource and rate limiting in API security, organizations should implement robust resource management and rate limiting mechanisms, including:
- Rate Limiting Policies: Define rate limiting policies to restrict the number of requests that can be made to API endpoints within a specified time frame, based on client identities, IP addresses, API keys, or other attributes. Implementing rate limits helps prevent abuse, control traffic spikes, and ensure fair usage of API resources.
- Throttling and Quotas: Implement throttling mechanisms to regulate the rate of incoming requests and enforce usage quotas to limit the amount of data or resources that clients can access or consume. Throttling helps maintain system stability, prevent resource exhaustion, and prioritize critical API requests during periods of high demand.
- Dynamic Rate Adjustment: Implement dynamic rate adjustment mechanisms that automatically adjust rate limits based on real-time traffic patterns, system load, or user behavior. Adaptive rate limiting enables APIs to scale capacity dynamically and respond to fluctuating demand while maintaining optimal performance and availability.
- Monitoring and Analytics: Deploy monitoring and analytics tools to track API usage patterns, monitor traffic metrics, and detect anomalies or suspicious activities indicative of abuse or DoS attacks. Proactive monitoring helps identify rate limit violations, unusual traffic patterns, or resource utilization spikes, enabling timely intervention and mitigation of security threats.
- Distributed Denial of Service (DDoS) Protection: Implement DDoS protection measures, such as traffic filtering, rate-based rules, or content delivery networks (CDNs), to mitigate the impact of volumetric DDoS attacks targeting API endpoints. DDoS protection solutions help mitigate large-scale attacks, maintain service availability, and safeguard API infrastructure from disruption.
Broken Function-Level Authorization
Broken Function-Level Authorization (BFLA) is a critical security vulnerability that occurs when APIs fail to enforce proper authorization controls at the function or endpoint level, allowing unauthorized users to perform privileged actions or access sensitive functionality that they should not have permission to execute. This vulnerability undermines the confidentiality, integrity, and availability of API resources, potentially leading to data breaches, unauthorized data manipulation, or system compromise.
BFLA vulnerabilities typically arise due to inadequate access control checks within API functions or endpoints, enabling attackers to exploit these weaknesses to gain unauthorized access to sensitive operations or manipulate application functionality. Attackers may leverage BFLA vulnerabilities to perform actions such as accessing administrative functions, deleting or modifying critical data, or executing unauthorized transactions.
To illustrate, consider an API endpoint that allows users to update their profile information. If the API does not properly validate the user’s authorization to perform this action, attackers could exploit this vulnerability to modify other users’ profile data, potentially compromising their privacy or integrity of their information.
Mitigating Broken Function-Level Authorization vulnerabilities requires implementing robust authorization mechanisms and access controls at the function or endpoint level. Key strategies for addressing BFLA vulnerabilities include:
- Role-Based Access Control (RBAC): Implement RBAC policies that define roles, permissions, and access levels for different user groups. Enforce these policies at the function or endpoint level to restrict access to authorized users only.
- Authorization Middleware: Use authorization middleware or interceptors to enforce access control checks before allowing API requests to access sensitive functions or endpoints. Validate user permissions and roles against the requested action to ensure proper authorization.
- Fine-Grained Access Controls: Implement fine-grained access controls that granularly define permissions for each API function or operation based on the user’s role, context, or other relevant attributes. This allows for precise control over who can perform specific actions within the API.
- Contextual Authorization: Implement context-aware authorization mechanisms that consider factors such as user attributes, resource ownership, or business rules when evaluating access requests. This ensures that access control decisions are made based on the specific context of each request.
- Input Validation and Sanitization: Validate and sanitize input parameters and data to prevent injection attacks, such as parameter tampering or command injection, that could be used to exploit BFLA vulnerabilities.
- Audit Trails and Logging: Maintain comprehensive audit trails and logging mechanisms to record user activities, access attempts, and function-level authorization decisions. Regularly review audit logs to detect and investigate suspicious behavior or unauthorized access attempts.
- Security Testing and Code Reviews: Conduct security testing, code reviews, and vulnerability assessments to identify and remediate BFLA vulnerabilities in API functions or endpoints. Ensure that access control checks are consistently applied and properly enforced throughout the API codebase.
Inadequate Logging and Monitoring
Inadequate logging and monitoring represent significant vulnerabilities in API security, posing risks to the detection, analysis, and mitigation of security incidents. Effective logging and monitoring are essential components of a robust security posture, providing organizations with visibility into API activities, detecting anomalous behavior, and facilitating timely response to security threats. When logging and monitoring practices are insufficient, organizations may fail to detect security incidents, leaving their API ecosystems vulnerable to exploitation and compromise.
One of the primary challenges associated with inadequate logging is the lack of visibility into API activities and events. Without comprehensive logs detailing API requests, responses, user activities, and system events, organizations may struggle to identify and investigate security breaches, unauthorized access attempts, or suspicious behavior. Inadequate logging may also hinder forensic analysis and incident response efforts, making it difficult to determine the root cause of security incidents or assess the extent of the damage.
Furthermore, insufficient monitoring exacerbates the problem by limiting real-time visibility into API traffic and activities. Without effective monitoring mechanisms in place, organizations may fail to detect security threats as they occur, allowing attackers to exploit vulnerabilities, exfiltrate data, or disrupt API operations without detection. Inadequate monitoring may also result in delayed incident response, giving attackers more time to escalate their attacks or cover their tracks.
You May Also Read : 12 Best Practices to Secure Your API in the AWS Cloud
API Security Best Practices
API security is of paramount importance in safeguarding sensitive data, ensuring data integrity, and maintaining the trust of users and stakeholders. Implementing robust API security best practices is essential for protecting against various threats and vulnerabilities that may compromise the confidentiality, integrity, and availability of API endpoints and data. Here’s an elaboration on API security best practices:
- Implement Access Control: Access control mechanisms are fundamental in ensuring that only authorized users or systems have access to protected resources. Implement role-based access control (RBAC), attribute-based access control (ABAC), or other access control models to define and enforce fine-grained permissions based on user roles, privileges, or attributes.
- Encrypt API Requests and Responses: Encryption is crucial for protecting sensitive data transmitted over the network. Require the use of HTTPS/TLS encryption to encrypt API traffic, ensuring that data exchanged between clients and servers is secure and cannot be intercepted or tampered with by attackers.
- Validate and Sanitize Input Data: Input validation and data sanitization are essential for preventing injection attacks, such as SQL injection or cross-site scripting (XSS). Validate and sanitize all input data received from clients to ensure it adheres to expected formats, types, and ranges, mitigating the risk of injection vulnerabilities.
- Implement Secure Authentication Mechanisms: Use strong and secure authentication mechanisms to verify the identities of users or systems accessing APIs. Implement protocols like OAuth 2.0 or OpenID Connect for delegated authorization and authentication, and enforce strong password policies, multi-factor authentication (MFA), or biometric authentication for user authentication.
- Enforce Least Privilege Principle: Follow the principle of least privilege to restrict access rights and permissions to the minimum level necessary for users or systems to perform their intended tasks. Limit access to sensitive resources or functionalities based on users’ roles, responsibilities, or business needs, reducing the attack surface and minimizing the impact of potential security breaches.
- Regularly Update and Patch APIs: Keep APIs up-to-date with the latest security patches, updates, and fixes to address known vulnerabilities and security issues. Regularly audit API dependencies, libraries, and third-party components for security flaws or vulnerabilities, and promptly apply patches or updates to mitigate risks.
- Implement Secure Logging and Monitoring: Implement comprehensive logging and monitoring mechanisms to track and analyze API activities, detect suspicious behavior, and respond to security incidents in real-time. Monitor API access logs, audit trails, and security events for unauthorized access attempts, abnormal usage patterns, or potential security breaches, and take appropriate action to mitigate risks.
- Conduct Regular Security Audits and Assessments: Perform regular security audits, vulnerability assessments, and penetration testing to identify and remediate security weaknesses, vulnerabilities, or misconfigurations in APIs. Engage with security experts or external auditors to assess API security posture, conduct threat modeling exercises, and implement security controls based on industry best practices and standards.
- Secure API Documentation and Communication: Protect API documentation, endpoints, and communication channels from unauthorized access or disclosure. Implement access controls, authentication mechanisms, or encryption for API documentation and communication channels (e.g., API gateways) to ensure confidentiality and integrity of API-related information.
- Educate and Train Developers: Provide ongoing security education and training to developers, architects, and other stakeholders involved in API development and management. Raise awareness about common security risks, best practices, and security guidelines for secure API design, development, and deployment, empowering teams to build secure and resilient APIs from the ground up.
You May Also Read : Next Generation of API Development: Transitioning from REST to GraphQL and gRPC
Conclusion:
Ensuring the security of APIs is paramount in today’s digital landscape where the exchange of data between systems and applications is ubiquitous. API security encompasses a range of best practices aimed at protecting sensitive data, preventing unauthorized access, and mitigating the risks posed by various threats and vulnerabilities. By implementing robust access control mechanisms, encrypting API traffic, validating input data, and enforcing secure authentication mechanisms, organizations can strengthen the security posture of their APIs and safeguard against potential attacks.
Furthermore, adherence to the principle of least privilege, regular updates and patching, implementation of secure logging and monitoring, and conducting regular security audits are vital components of a comprehensive API security strategy. Educating and training developers on security best practices also plays a crucial role in fostering a security-conscious culture within organizations.
Ultimately, by prioritizing API security and adopting a proactive approach to addressing security risks, organizations can enhance trust, protect sensitive data, and ensure the integrity and availability of their API ecosystems. In an increasingly interconnected world, robust API security practices are essential for safeguarding digital assets and maintaining the confidence of users and stakeholders.

















