Django Security Checklist: Must-Do Steps for a Safe Web Application
Table of Contents
In today’s digital landscape, web application security is vital. With cyber threats constantly evolving, safeguarding your web application against vulnerabilities and attacks is not just recommended; it’s imperative. Django, a high-level Python web framework, is well-regarded for its security features. However, the complexities of modern Django-based web applications demand a layered approach to protection.
Understanding and implementing the best security practices is vital for expert Django developers. It’s about more than just writing clean code; it’s about integrating security measures into every phase of the development process. A comprehensive security checklist can be a crucial tool, guiding developers through the necessary steps to secure their applications effectively. It’s not just about protecting data; it’s about building trust with users and maintaining the integrity of the Django ecosystem. Here are the key steps you need to follow to ensure your web application is strong and secure.
Why Does Django Security Matter?
Django security matters because it forms the foundation for a safe web application environment. Here are the reasons highlighting the importance of Django security:
- Protection of Sensitive Data: Django security protocols safeguard sensitive user data, ensuring its confidentiality and integrity. This is crucial for maintaining trust and complying with privacy regulations.
- Prevention of Vulnerabilities: By following Django’s security guidelines and best practices, you can proactively prevent common vulnerabilities such as XSS, CSRF, and SQL injection, reducing the risk of exploitation.
- Trust and Reputation: A secure web application builds trust among users and stakeholders. Trust is a valuable asset affecting user retention and the application’s reputation.
- Legal Compliance: Following Django’s security principles helps ensure legal compliance with data protection regulations, avoiding potential legal consequences.
- Cost-Effective: Addressing security concerns early in the development process is more cost-effective than dealing with security breaches and their aftermath.
- Continuous Improvement: Django’s continual evaluation and updates reflect its commitment to security. Stay informed about Django’s security practices ensures that your application remains strong against evolving threats.
How to Ensure Security in Django-based Web Applications?
Following are the things to do to ensure security in Django-based web applications:
1Set Up a Strong Foundation
A strong foundation is vital for the security and efficiency of your Django web application. It involves choosing a reliable hosting provider, ensuring correct web server configuration, and keeping your software up-to-date.
-
Choosing a Reliable Hosting Provider
Look for a hosting provider with a strong focus on security features, reliability, compliance with standards, and excellent customer support. Providers should also offer scalable resources and robust backup and disaster recovery options.
-
Ensuring Proper Configuration of Web Servers
Use trusted servers like Nginx or Apache and configure them for maximum security:
- Implement HTTPS and SSL/TLS encryption.
- Hide server version details.
-
Restrict access to sensitive URLs and directories.
For Django, set:
SECURE_SSL_REDIRECT = True SESSION_COOKIE_SECURE = True CSRF_COOKIE_SECURE = TrueFor Nginx:
server_tokens off;For Apache:
ServerTokens Prod ServerSignature Off
-
Regularly Updating Django and Dependencies
Keep Django and all dependencies up to date to protect against known vulnerabilities:
- Regularly check for and install updates for Django and third-party packages.
- Use virtual environments like ‘venv’ or ‘pipenv’ to manage dependencies.
- Test updates in a staging environment before deploying them to production.
By addressing these three key areas, you can establish a secure and stable foundation for your Django web application, reducing potential security risks.
2User Authentication
User authentication is an important aspect to consider for Django web application security. Here are the key elements to focus on:
-
Strong Password Policies
Ensure robust password security by enforcing complexity rules, offering clear password creation guidelines, and relying on Django’s automatic password hashing.
-
Multi-Factor Authentication (MFA)
Enhance security with MFA by integrating third-party packages like ‘django-otp’, providing diverse verification methods, and securely managing MFA secrets.
-
Secure User Sessions
Implement secure session management using Django’s built-in features, set brief session timeouts, and regenerate sessions post-login to counter session-based attacks.
-
Manage User Permissions and Roles
Define user access levels with Django’s role-based system, following the principle of least privilege to limit permissions, and conduct regular audits to maintain access control integrity.
By addressing these aspects, you can establish a robust foundation for user authentication and access control, elevating the overall security of your Django web application.
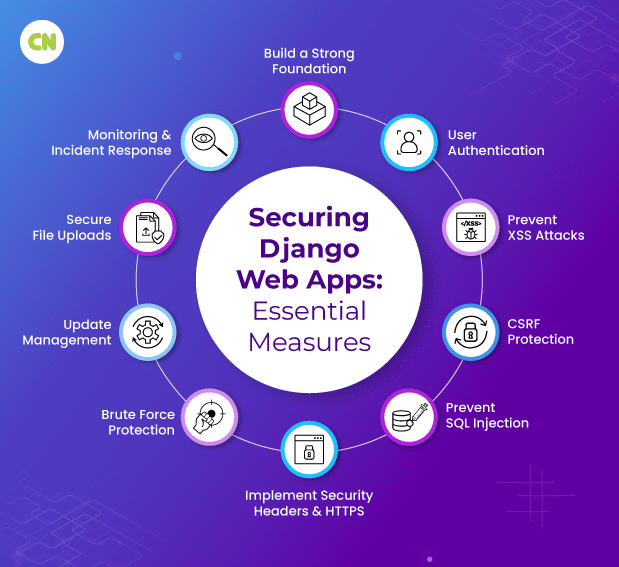
3Cross-Site Scripting (XSS) Prevention
-
Understanding XSS Attacks
XSS attacks involve malicious scripts injected into a web application, which are later executed in the context of the victim’s browser. It can lead to data theft, session hijacking, and more.
-
Proper Validation and Sanitization
To prevent XSS, thoroughly validate and sanitize user inputs:
# Use Django's built-in methods to escape HTML entities from django.utils.html import escapeinput_data = "<script>alert('XSS Attack');</script>" safe_input = escape(input_data) -
Implementing Content Security Policies (CSP)
Use CSP to restrict the sources of executable scripts in your web application:
<meta http-equiv="Content-Security-Policy" content="default-src 'self'; script-src 'self' trusted-scripts.com;">By understanding XSS attacks, validating and sanitizing user inputs, and implementing CSP, you enhance your Django application’s defense against this prevalent security threat.
4Cross-Site Request Forgery (CSRF) Protection
-
Understanding CSRF Attacks
CSRF attacks trick users into executing malicious actions on web applications without their consent. These attacks can lead to data manipulation, unauthorized actions, and account compromises.
-
Using Django’s Built-in CSRF Protection
Django provides robust CSRF protection out of the box. Simply add the ‘{% csrf_token %}’ template tag to your forms:
<form method="post"> {% csrf_token %} <!-- Your form fields here --> <button type="submit">Submit</button> </form>Django packages like ‘django-crispy-forms’ can further streamline CSRF protection.
-
Preventing CSRF Attacks
Follow these practices to enhance CSRF defense:
- Limit the use of ‘GET’ requests for actions with side effects.
- Ensure the usage of secure cookies (‘SESSION_COOKIE_SECURE’ and ‘CSRF_COOKIE_SECURE’ settings).
-
Implement SameSite cookie attributes for modern browsers:
SESSION_COOKIE_SAMESITE = "Lax" CSRF_COOKIE_SAMESITE = "Lax"
By leveraging Django’s built-in CSRF protection, incorporating Django packages, and following best practices, you can safeguard your web application against CSRF vulnerabilities.
5SQL Injection Prevention
-
Understanding SQL Injection Vulnerabilities
SQL injection occurs when malicious SQL code is inserted into input fields or requests, potentially allowing attackers to manipulate or access the database. This can lead to data leaks and unauthorized actions.
-
Using Django’s ORM for Safe Database Interactions
Django’s Object-Relational Mapping (ORM) provides a secure way to interact with databases. It automatically escapes input and prevents SQL injection:
# Using Django ORM to filter a model from myapp.models import User username = "malicious_username'; DROP TABLE users;" user = User.objects.filter(username=username).first() # Automatically sanitized by ORM -
Prepared Statements and Parameterized Queries
If you need to write raw SQL queries, use parameterized queries to insert user input safely:
# Using parameterized queries in Django from django.db import connection cursor = connection.cursor() sql = "SELECT * FROM myapp_user WHERE username = %s" username = "malicious_username'; DROP TABLE users;" cursor.execute(sql, [username]) # Safely sanitized
By relying on Django’s ORM for database interactions and implementing parameterized queries, you mitigate the risk of SQL injection vulnerabilities in your Django web application.
6Secure File Uploads
-
Risks Associated with File Uploads
File uploads can introduce security risks if not handled properly. Attackers may upload malicious files to compromise your web application, leading to various vulnerabilities, including code execution and data leakage.
-
Validating File Types and Extensions
To mitigate risks, validate file uploads by checking file types and extensions:
from django.core.exceptions import ValidationError from django.utils.translation import gettext as _ def validate_file_extension(value): valid_extensions = ['.jpg', '.png', '.pdf'] # Define acceptable file extensions file_extension = os.path.splitext(value.name)[1] if file_extension not in valid_extensions: raise ValidationError(_('Invalid file extension.')) -
Storing Uploads Securely
Store uploads in a location separate from the web root directory to prevent direct access:
# In settings.py MEDIA_URL = '/media/' MEDIA_ROOT = os.path.join(BASE_DIR, 'media/')
By following these practices, you ensure secure file uploads in your Django web application, protecting it from potential threats.
7Protecting Against Brute Force Attacks
-
Understanding Brute Force Attacks
Brute force attacks involve automated attempts to guess passwords, posing risks to your web application. If successful, attackers can gain unauthorized access, compromise accounts, and potentially steal sensitive data.
-
Implementing Rate Limiting and Account Lockout Mechanisms
Prevent brute force attacks by implementing rate limiting and account lockout mechanisms:
# In settings.py, set login rate limits and lockout settings LOGIN_RATE_LIMIT = '5/m' LOGIN_FAILS_LIMIT = 5 LOGIN_FAILS_TIMEOUT = 300 # 5 minutes # In views.py, use Django's built-in decorators from django.contrib.auth.decorators import login_required, login_limit @login_limit(key="username", rate=LOGIN_RATE_LIMIT, method="POST") def login_view(request): # Your login view logic here -
Monitoring and Logging Failed Login Attempts
Maintain visibility into login activity by monitoring and logging failed login attempts:
# In settings.py, configure logging LOGGING = { 'version': 1, 'disable_existing_loggers': False, 'handlers': { 'failed_login': { 'level': 'DEBUG', 'class': 'django.utils.log.AdminEmailHandler', }, }, 'loggers': { 'django.security': { 'handlers': ['failed_login'], 'level': 'DEBUG', 'propagate': False, }, }, }
By implementing these measures, you can save your Django web application against brute force attacks, helping safeguard user accounts and sensitive data from unauthorized access.
8Regular Updates and Patch Management
-
Importance of Keeping Django and Third-party Libraries Up to Date
Regularly updating Django and third-party libraries is crucial for security. Updates often include security patches that address vulnerabilities discovered since the previous version. Staying current helps protect your web application from known threats:
# To update Django and packages pip install --upgrade django django-packages -
Setting Up Automated Update Checks
Automate the process of checking for updates using tools like pip-tools and a version control system:
# Install pip-tools pip install pip-tools # Create and update a requirements.in file # Use 'pip-compile' to generate a requirements.txt file pip-compile # Add 'requirements.txt' to your version control system -
Testing Updates in a Staging Environment
Before applying updates to your production environment, thoroughly test them in a staging environment to ensure they do not introduce any unexpected issues:
# Set up a staging environment for testing # Apply updates and thoroughly test your application # Monitor for any compatibility or functionality issues
By following these practices, you maintain the security and stability of your Django web application, reducing the risk of vulnerabilities and ensuring smooth operation.
9Security Headers and HTTPS
-
Understanding Security Headers (e.g., HSTS, X-Frame-Options)
Security headers are HTTP response headers that enhance your web application’s security. Key headers include:
-
HTTP Strict Transport Security (HSTS): Instructs browsers to load your site securely over HTTPS, preventing protocol downgrade attacks.
# In Django settings.py SECURE_HSTS_SECONDS = 31536000 # Set HSTS policy for one year SECURE_HSTS_INCLUDE_SUBDOMAINS = True -
X-Frame-Options: Prevents your site from being loaded in an iframe, mitigating clickjacking attacks.
# In Django settings.py X_FRAME_OPTIONS = 'DENY'
-
-
Enforcing HTTPS for Secure Communication
HTTPS encrypts data exchanged between the user and the server, safeguarding it from interception and tampering. Obtain an SSL certificate and enforce HTTPS:
# In Django settings.py SECURE_PROXY_SSL_HEADER = ('HTTP_X_FORWARDED_PROTO', 'https') # If behind a proxy SESSION_COOKIE_SECURE = True CSRF_COOKIE_SECURE = True -
Configuring Web Server and Django Settings
Ensure your web server (e.g., Nginx, Apache) is properly configured to serve HTTPS, and set Django security settings as needed:
# Nginx configuration (example) server { listen 443 ssl; server_name yourdomain.com; ssl_certificate /path/to/ssl/certificate; ssl_certificate_key /path/to/ssl/private/key; location / { # Django application settings here } }
By using these security headers, enforcing HTTPS, and configuring your web server and Django settings correctly, you can enhance the security and privacy of your Django web application.
10Monitoring and Incident Response
-
Implementing Security Monitoring Tools
To proactively identify security threats, implement monitoring tools like Django Debug Toolbar, Sentry, or third-party security services:
# Install and configure Django Debug Toolbar pip install django-debug-toolbar # In settings.py MIDDLEWARE = [ # ... 'debug_toolbar.middleware.DebugToolbarMiddleware', ] # Configure Sentry for error tracking # Install the Sentry SDK and set DSN in settings.py -
Setting Up Alerting for Suspicious Activities
Configure alerting mechanisms to notify you of unusual or suspicious activities. You can use Django’s logging system to trigger alerts:
# In settings.py LOGGING = { 'version': 1, 'disable_existing_loggers': False, 'handlers': { 'security_alerts': { 'level': 'ERROR', 'class': 'your_alerting_handler.AlertingHandler', }, }, 'loggers': { 'django.security': { 'handlers': ['security_alerts'], 'level': 'ERROR', 'propagate': False, }, }, } -
Developing an Incident Response Plan
Create an incident response plan that outlines steps to take when a security incident occurs:
- Define incident severity levels and response procedures.
- Define incident severity levels and response procedures.
- Communicate the plan to your team and ensure everyone understands their responsibilities.
By using monitoring tools, setting up alerts, and having an incident response plan in place, you can identify and mitigate security incidents.
Read More: Django, Flask, FastAPI: A Comparative Analysis of Python Web Frameworks
Final Thoughts
Securing a Django web application needs a comprehensive approach, blending robust measures like user permission management, protection against XSS, CSRF, SQL injection, and vigilant file upload handling. But security doesn’t stop at setup; it’s an ongoing process. Regularly updating Django and third-party libraries, enforcing HTTPS, and setting up security headers are critical for maintaining a strong defense against emerging threats.
However, the technical setup is only part of the story. A robust security measure also demands proactive monitoring and a strategic incident response plan. By maintaining alertness, updating your security measures regularly, and preparing to address potential issues promptly, you can ensure that your Django application stands secure and remains a dependable resource for your users.