Blockchain Breakthroughs: Transforming Authentication, Authorization, and Accounting
Table of Contents
Blockchain has gained immense popularity in the tech world nowadays. But is blockchain worth such hype? Before understanding blockchain and its functioning in detail (technically), let’s analyze a real-world banking system for a basic understanding of how blockchain profits various related identities. Assume there is a bank called ‘X’ giving services to Wang, Nicolos and Andreas. Andreas and Nicolos are office colleagues and are regular customers of a Chinese restaurant run by Wang. One Saturday night, they decided to have some Chinese, and Wang’s restaurant was the obvious choice. After having a decent dinner, they asked for the bill and opted to pay online. Due to some issues, Nicolos requested Andreas to pay for him and assured him that pay him later. Andreas obtained the address (i.e., Anything that refers to the bank account number of Wang) from reception and paid the stated amount (the amount included the cost of the eatables they both had). The next day, Nicolos decided to pay Andreas for the last night and used the same bank service to pay Andreas.
In the above story, there are two sections where entities are interacting with each other online. First, Andreas is paying to Wang, and second, Nicolos is paying to Andreas. Before starting anything, let’s consider these questions for both scenarios. Who assures that the recipient addresses obtained by Andreas and Nicolos in both scenarios are designated to their desired address? (authenticity) and what is a guarantee that the amount paid to Andreas and Nicolos belongs to them? (authorization). The obvious answer is ‘X'(i.e., the bank), and no one will oppose this. But in this whole scenario, the fact that the whole trust among entities depends solely on the bank ‘X’ is also true. No matter what you do while you interact with other entities, the entire process will be governed by a solo source, that is, the bank here. Now, what if I say there is a technology called Blockchain that will not only profit entities regarding these issues but will also help the banks reduce their workload?
“The blockchain is an incorruptible digital ledger of economic transactions that can be programmed to record not just financial transactions but virtually everything of value.” – Don & Alex Tapscott, authors Blockchain Revolution (2016).
1. Understanding Blockchain
Blockchain is a series of records of data that are immutable in nature, which is governed by a cluster of systems that are interconnected with each other and are not owned by a single entity, explaining why blockchain is a decentralized system (there is no central authority). The first ever blockchain was invented by Satoshi Nakamoto in 2008 and later was implemented as the first cryptocurrency called ‘Bitcoin’. We don’t have a central governing authority; what about authentication and authorization discussed earlier? How can blockchain provide a solution to those issues?
The answer lies in the architecture of blockchain. Authentication is the procedure followed to prove something (i.e., Anything considered) is real or valid. Simply stating authentication is verifying the identity of any user in the blockchain. Authorization is the process of providing access rights to the data or value that is being considered as per the situation. Want to know about these in detail before opting for blockchain development services? Let’s dive in.
2. Why Are Blockchain-based Authentication and Authorization Important?
This is an important question to answer before understanding how blockchain helps in authorization and authentication. Let’s consider Electronic Commerce (E-Commerce) to understand its importance. E-commerce has grown drastically in these few years and are playing a major role in people’s life. For any E-commerce site, privacy and security will always be major concerns as data regarding the product being bought and money paid for the product are all done online.
Consider an E-commerce site, ‘XYZ,’ which is famous for buying gadgets. Imagine yourself going for a vacation with your friends while you just come out of your house to join your friends for the proceeding, your phone rings, prompting a message from your bank regarding the amount that has been paid from your bank for the objects you didn’t even buy, but it would be hard to explain it right. For any system, authentication and authorization are among the most important features, as these two things represent your virtual identity for that system.
3. Methods Used for Authentication Nowadays
Various systems use different authentication methods for the users. But all have one thing in common; they all require a certain initial to do so. Various systems ask for different initials for using authentication, for example, things known by users such as passwords, biometrics, tokens, smart cards, etc.
3.1 Drawbacks related to passwords as initials
While authenticating yourself in a particular system, you simply type down your initials. Now, in this particular situation, what are various ways of attacking the user? If you are in touch with the cyber security field, you must have come across attacks like spoofing and keylogging. Apart from these technical attacks, methods like social engineering and random guessing of passwords may also work if you are a bit close to the victim.
For those who are unfamiliar with the terms,
- Spoofing: When a hacker tries to impersonate another user of the system so that he or she can get control over the user’s data.
- Key-logging: This is generally a script running in the background of your computer capable of fetching all the characters that are being typed by your keyboard with the respective typing time. These scripts can be manifested in your computer by hackers through any removable media or wirelessly.
- Social-Engineering: This method cannot be considered a solely technical attack. Hackers try to make you reveal your password verbally or through various methods like a random message in your phone stating an update in your bank account for which it requires your account details.
4. Authentication and Authorization in Blockchain
Ownership of data regarding any blockchain is established through digital keys, digital signatures, and the address of the owner and recipient. In this section, the mechanism is a reference from the architecture of Bitcoin so that you can understand blockchain through one of its implementations.
The digital keys for Bitcoin or any blockchain are generally created by the user and can be stored anywhere in terms of Bitcoin, they have a database to store these keys known as a wallet. Bitcoin uses asymmetric or public key cryptography (invented in the 1970s). After the invention of public key cryptography, several mathematical functions, practically irreversible, were invented to support this cryptography. One of those mathematical functions is the elliptic curve equation.
4.1 Elliptic Curve Equation
An elliptic curve is a curve that, when represented on the graph, would have all the points satisfying the equation,
This equation, when represented using a graph, would have singular points. To avoid those singular points, equation 4a3 +27b2 ≡ 0 should be satisfied. Any elliptic curve following the above pattern will always be symmetrical about the x-axis. For proof, let’s take the equation above and consider x=2, a=3, and b=2, and take the square root on both sides of the equation. We obtain two points (2,4) and (2, -4) when we solve the equation, representing values of x and y. No matter what values a, b, and x have, y will always have positive and negative values, proving that the curve is symmetrical to the x-axis.
The elliptic curve math has a point called “Point at infinity“. The simpler meaning of this term is 0. Generally represented by x-y=0.
If two points, ‘P’ and ‘Q’ are taken on the elliptic curve, then there must be one more point that is obtained after adding ‘P’ and ‘Q’. Let’s consider that point as ‘R’.
To draw this line geometrically, first, we have to join the points ‘P’ and ‘Q’. This line will intersect the elliptic curve in exactly one additional place. This place is called ‘-R’, having coordinates (x, y). Now the coordinates of ‘-R’ are reflected along the x-axis to obtain R (just multiply y of ‘-R’ with -1).
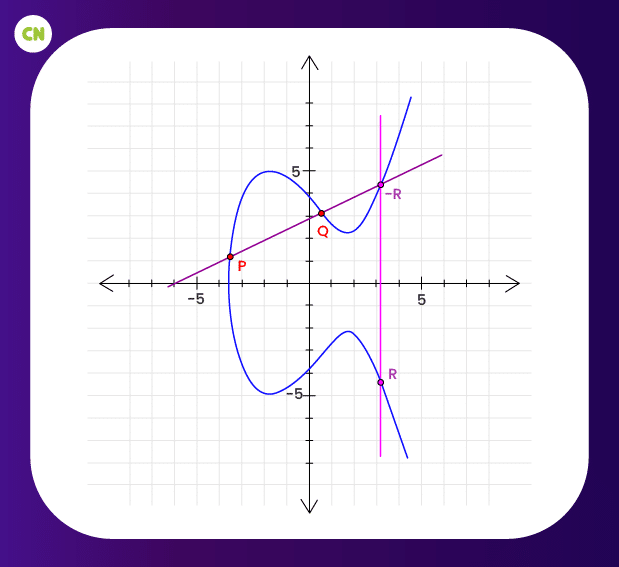
Elliptic Curve Showing the Addition of Two Points on the Curve
There are a couple of special cases that explain the need for the “point at infinity.”
Let’s consider ‘P’ and ‘Q’ representing a single point. Now, there are infinite lines possible, but for convenience, only the tangent of that point is considered. This tangent will intersect the curve at exactly one new point. If both the points have a value of x common but a different value of y. Then the line joining them would be vertical, and ‘R’ would be the “point of infinity”.
Let’s consider ‘P’ to be the “Point of infinity”. Now when we add P and Q we get Q (the answer will be P if Q is the “Point of infinity”). Similarly, multiplication can also be defined by modified standard addition. For a point P on the elliptic curve, if n is a whole number, then nP = P + P + P + …+ P (n times).
The elliptic curve used by blockchain is secp256k1, having its mathematical constants. secp256k1 can be represented by the following function:
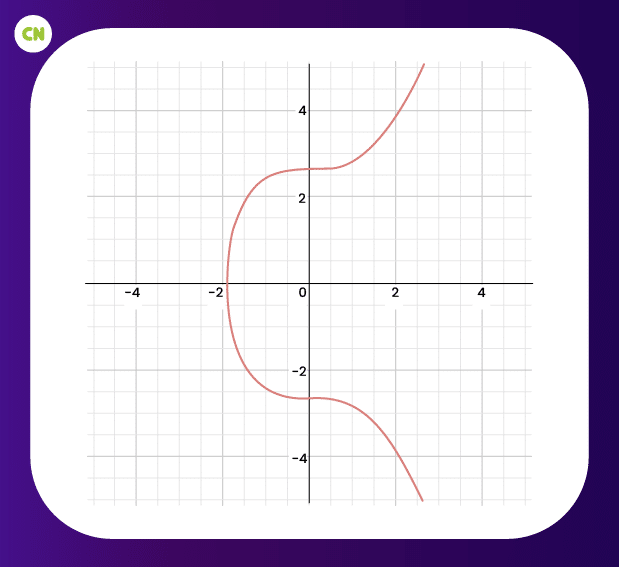
Elliptic curve of Bitcoin
4.2 Authentication
This issue can be solved with the help of keys. At first, the user has to generate private and public keys. These sets of keys are generally never present in the network but are kept in the wallet, and the network protocols do not affect these keys. The public key is generally used to refer to the user’s network address. We can say that the public key of a user can be a digital fingerprint for its address. Authentication, as well as authorization, is generally verified with the help of the private key. Consider a situation where user-1 and user-2 are in a blockchain network, and user-1 is trying to send data to user-2. In this scenario, when user-2 obtains the data, how will the user be sure that the obtained data has been sent by user-1? The answer to this question is the private key of user-1, which is used by user-1 to sign or, we can say, generate a digital signature that can used to access the data and also verify that the obtained data is transferred from user-1 (legitimate user). What if user-2 tries to obtain the private key of user-1 from the digital signature? This is also impossible as the algorithm used to generate this digital signature is always a one-way function. It means one can obtain as many digital signatures from a private key but can never get the private key from the digital signatures.
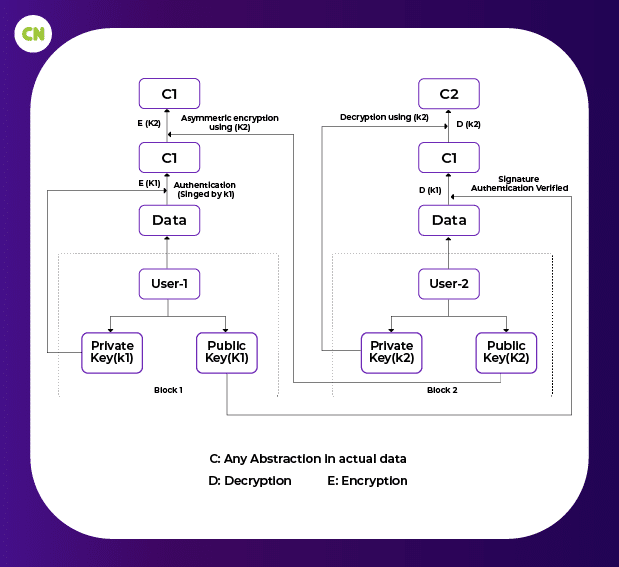
Basic structure of data transfer in blockchain
4.3 Authorization
After signing the data with his or her private key, user-1 uses Elliptic Curve Cryptography to encrypt the data again before sending it to user-2, and user-1 does this by using asymmetric encryption. Here user-1 encrypts the data using user-2’s public key, because of which the only legitimate user (user-2) has the authority to access the data. This encryption has to be done so that the transfer of authorization over the data is conducted properly, and except for user-2, no one else has the medium to access the data.
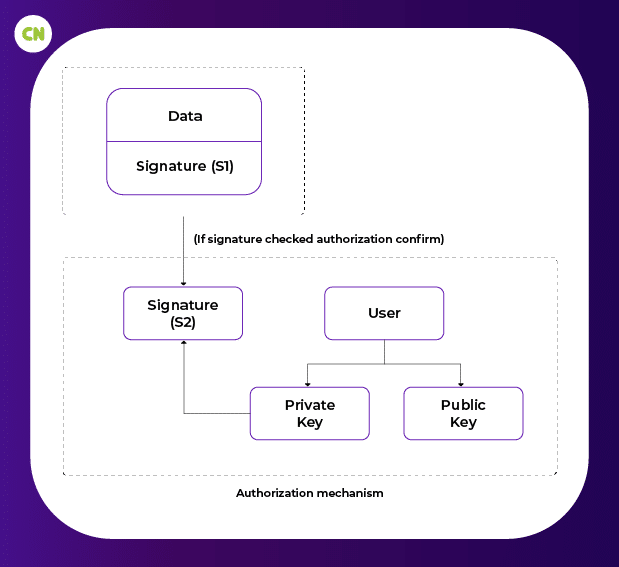
Authorization mechanism
4.4 Private Key
A private key is simply a number picked at random. Bitcoin uses the underlying operating system’s random number generator to produce 256 bits of the private key (tossing a coin 256 times with heads and tail given binary values, we have the binary digit of the private key, which is a random selection). Keeping the private key safe is very important, as losing the key would give away all the information protected by the private key. Private Key is generally used to generate signature, which is used to authorize data transfer.
4.5 Public Key
A public key is generated by a private key using elliptic curve multiplication. Which is irreversible in nature. Consider the private key to be k. In Bitcoin, there is a constant point G which is called the generator point. G is a constant defined in secp256k1. Let’s take variable K to be the public key which is obtained as K=k*G.
We multiply k with G to produce another point on the graph; this referred point is called the public key. Bitcoin generally uses the public key to generate a Bitcoin address.
4.6 Address Generation
The most common use of an address is to know the owner of the private and public keys, but it can also refer to something else, for example, a payment script. An address is generally derived from the public key with the help of a one-way hash function. A hash function is a mathematical function that is easy to do in one direction but practically impossible to reverse. Bitcoin uses SHA256 and RIPEMD160 to produce the address. At first public key is taken as input to SHA256 to produce a hash of 256 bits, and the output is given RIPEMD160 to produce 160 bits of public key.
Address=RIPEMD160(SHA256(K))
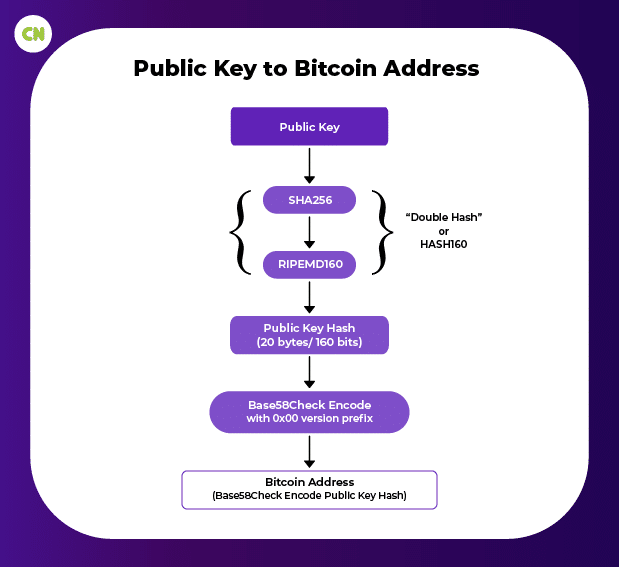
Procedure to generate Bitcoin address with public key
4.7 Encoding
The private and public key values shown to the user are generally not the actual keys. Actually, what you see are keys but are in encoded format. Encoding is done to represent long values in compact form. Every encoding format has its own set of characters that replace the actual values like hex, Base64, etc. Base64 is an encoding method represented by the values 26 lowercase letters, 26 capital letters,10 numerals, and 2 more characters such as ‘+’ and ‘-‘. Bitcoin uses Base58check encoding which has its own error-checking code. Base58 is a subset of Base64, removing all characters which look alike (0,O,l,I).
To convert any data into Base58check format, we first have to add a prefix to the data; this particular data is version byte, usually signifying the type of data. For example, 0(0x00 in hex) will be the prefix for Bitcoin address and 128(0x80) for private keys.
The next step is to obtain the checksum. To generate the checksum, we apply SHA256 twice on prefix+data. The obtained value will be a 32-byte hash; from this 32-byte value, we only take 4 byte of value from the start and add it as a suffix of data. This 4-byte value that we add as a suffix is known as the checksum. After joining version byte + data + checksum, the characters obtained are later encoded in Base58 format.
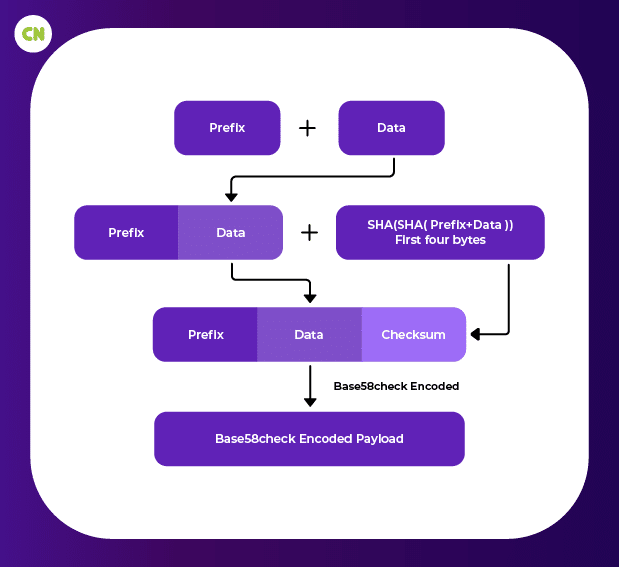
Data encoding in Base58check
5. Limitations of Blockchain
Every technology has some issues, whether it is regarding security, space consumption, or complexity of algorithms, and blockchain is no different. Below are a few of the issues blockchain has to go through,
5.1 Throughput Challenges
One of the major weaknesses of blockchain is its low throughput. The distributed ledger system can only move information from one point to another at a maximum speed pre-defined. For example, Bitcoin has the speed and power of processing seven transactions per second. However, data transferred within the network is not necessarily sent at that speed. As we have seen with Bitcoin in early 2016, it used to take 45 minutes to do a particular transaction.
5.2 Blockchain uses an excessive amount of energy
Miners or mining companies, who are competing for the creation of the next block in the blockchain, use a significant amount of computational power, and to obtain that power high amount of electricity is being used. In a world where electricity is a climate issue, the processing mechanism of blockchain makes less sense.
5.3 The anonymous characters of blockchains don’t always act like an asset
Considering a system with various users, the fact that a legitimate user can be the most dangerous attacker can never be denied in this situation. Considering Bitcoin, every user is authorized to see everything happening in the network. Therefore, the system lacks anonymity; instead, they added pseudo randomity, which is insufficient. For example, a company wants to have a deal with one of its users and decides to pay via Bitcoin. The company transfers funds to the recipient’s address. Now the possibility is that the recipient knows about the company’s account balance. This issue may seem small, but personal information may not be important for individuals, but for business, it’s a different thing.
5.4 Inefficiency regarding offline usage
This is also a problem that was seen in Bitcoin. Bitcoin users have to store their blockchain data in their wallets; generally, this data exceeds 100 GB of data. To use the wallet offline, downloading the blockchain data is important, and this whole process of downloading and verification sometimes takes a couple of days.
5.5 Security issues faced by blockchain
5.5.1 The majority attack or 51% attack
This attack is not a cyber attack but rather a situation that can arise further, leading to malicious transactions being circulated to users. Bitcoin, for example, is dependable on miners for confirming transactions. They use a consensus algorithm to prove the work for adding their blocks to the blockchain. If an organization takes control over most of the network (generally considered when more than 50% of the network is under the influence), it could use a particular transaction more than once, which means the organization can spend n times the amount with the same transactions.
6. Blockchain Implementation in Full-Scale
Distributed ledger architectures are scalable; any changes ever made to the blockchain will result in scaling up. A couple of changes are more like this, and we obtain an added block in the network. Every blockchain ever considered is scaling up daily, and no major issues are showing up. But what about the time when blockchain will be implemented on full scale?
According to the Financial Stability Oversight Council (FCOS), the world is approaching an unknown territory regarding space consumption (expansion by a single gigabyte). It is a major concern as no company is well-versed with every possible problem that may occur shortly. Due to this lack of experience, we must upgrade ourselves with the current tech trends and move accordingly.
Bottom Line
In the dynamic landscape of digital security, blockchain technology is introducing robust and decentralized methods for authentication, authorization, and accounting. It leverages blockchain’s transparency and immutability to improve digital identity security and streamline authorization, leading to more reliable digital interactions. Also, blockchain integration in accounting offers unparalleled accuracy and transparency, revolutionizing traditional financial systems.
Do you want to build a custom Blockchain app? Opt for Capital Numbers, an award-winning software solutions company offering end-to-end development services globally. Want to discuss your project? Book a call today!