API Security Best Practices to Protect Your Applications from Threats
Table of Contents
APIs are the backbone of modern software systems. They allow different applications and services to communicate with each other, enabling everything from mobile apps to cloud platforms to function smoothly. However, with this power comes risk. APIs, if not properly secured, can become easy targets for attackers, leading to serious security breaches, data leaks, and service disruptions.
For developers and companies seeking API development services, understanding API security is crucial to protecting applications from these threats. Securing APIs not only safeguards your app but also ensures the safety of your users’ data.
The goal of this blog is to explain the importance of API security and provide guidance on how to protect your applications from common API-related threats. We’ll discuss vulnerabilities, best practices, and tools that can help you safeguard your APIs against attacks. By the end, you’ll be equipped with the knowledge needed to effectively secure your APIs and enhance the overall security of your applications.
Understanding API Security
What is an API?
An API (Application Programming Interface) is like a messenger that helps different software applications communicate with each other. Think of it as a bridge that allows one program to send or request information from another. For example, when you use a mobile app to check the weather or book a ride, the app is using an API to get the information from another system or service.
Why APIs are a Target for Attackers
APIs are attractive to attackers because they act as a direct gateway to valuable data and services. Here are two main reasons why APIs are targeted:
- APIs expose sensitive data: APIs provide access to important data, such as user details, financial transactions, or business operations. If an attacker can break into an API, they can steal or misuse this data.
- Widespread use: As more companies rely on APIs across various industries (from banking to healthcare), the number of APIs in use has exploded. This increase means there are more opportunities for attackers to find weaknesses and exploit them.
Key Security Concerns for APIs
When thinking about API security, you need to be aware of several risks:
- Unauthorized Access: If security measures are weak, hackers can access the API without permission and steal data or manipulate the system.
- Data Breaches: Poorly protected APIs can expose sensitive data like personal information, financial details, or proprietary business data.
- DDoS (Distributed Denial of Service) Attacks: Attackers can overwhelm an API with a flood of requests, causing the service to slow down or stop functioning.
- API Abuse and Misuse: Sometimes, even legitimate users might misuse APIs by making too many requests or using them in ways that were not intended, which can disrupt services or cause performance issues.
By understanding these risks, you can build more secure APIs and better protect your applications.
Best Practices to Secure Your APIs
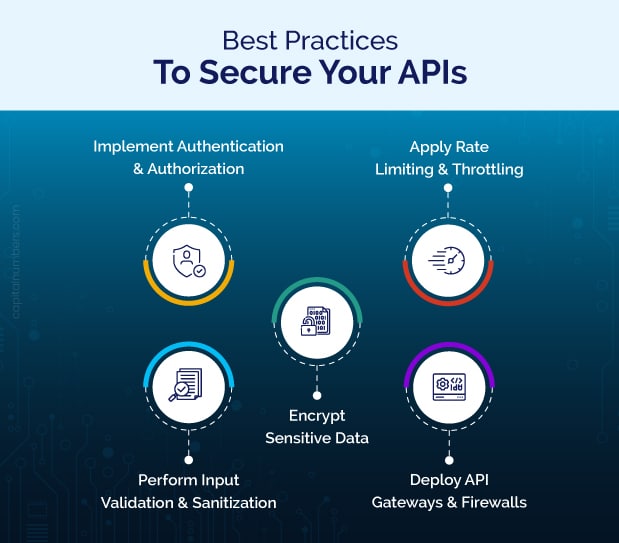
1. Use Strong Authentication and Authorization
You need to make sure that only the right people can access your API. Here’s how you can do that:
- OAuth 2.0 and OpenID Connect: These are secure methods for verifying the identity of users. OAuth 2.0 allows users to log in securely using accounts from platforms like Google or Facebook without sharing their passwords. OpenID Connect is built on top of OAuth 2.0 and adds more security by verifying user identities.
- Role-Based Access Control (RBAC): RBAC ensures that users can only access the parts of your API that are relevant to their roles. For example, an admin might have access to more API functions than a regular user.
- Scope Validation: This involves checking what actions or resources a user is allowed to access based on their permissions (scope) and ensuring they don’t exceed those limits.
2. Encrypt Data
Always protect the data traveling between clients (like web browsers or mobile apps) and your API:
- TLS (HTTPS): You should always use HTTPS (which uses TLS encryption) to make sure the communication between clients and your API is secure. This prevents attackers from intercepting sensitive information.
- Encryption for Sensitive Data: Not only should you encrypt data while it’s being sent (in transit), but you should also encrypt it when it’s stored (at rest) to protect it from being accessed by unauthorized users.
3. Rate Limiting and Throttling
You need to prevent users or attackers from overloading your API with too many requests, which could crash your system or make it slow.
- Rate Limiting: This limits how many times a user or system can call your API within a certain time frame. This can protect you from abuse, such as DDoS (Distributed Denial of Service) attacks where attackers flood your API with requests.
- Throttling: If a user exceeds the rate limit, you can slow down (throttle) their access to the API rather than completely block them. This helps ensure fair usage.
4. Input Validation and Sanitization
Make sure all input coming into your API is safe and clean:
- Input Validation: Before processing any data from users, verify that the data is in the correct format and doesn’t contain anything unexpected. For example, if a field expects a number, make sure the input is actually a number.
- Sanitization: This involves cleaning the input to remove potentially harmful characters or code (like scripts or SQL commands). This helps prevent attacks such as SQL injection or cross-site scripting (XSS).
5. API Gateway and Firewalls
These tools act as guards for your API, adding an extra layer of security:
- API Gateway: An API gateway sits between users and your API, managing things like authentication, authorization, and monitoring. It acts as a single point of entry, making it easier to enforce security policies across all API requests.
- Web Application Firewall (WAF): A WAF helps detect and block malicious traffic before it reaches your API. It can protect your API from common attacks such as SQL injection or DDoS attacks by analyzing incoming traffic and filtering out anything harmful.
By following these best practices, you can make your APIs much more secure and reduce the risk of attacks or data breaches.
Secure API Design Principles
1. Principle of Least Privilege (PoLP)
This principle means that your API should only be allowed to access the data and resources it absolutely needs, and nothing more. By restricting access, even if someone hacks your API, the amount of damage they can do will be limited.
- Example: If your API is meant to show user profiles, it should only be able to access profile information and not have access to things like payment details or admin settings. By limiting access, you reduce the risk if something goes wrong.
2. Secure API Endpoints
API endpoints are the specific URLs or addresses where your API can be accessed (like https://yourapi.com/user/profile). Securing these endpoints is crucial to protect your API from attacks.
- SSL/TLS Encryption: Always use SSL/TLS (i.e., HTTPS) to encrypt the communication between your API and its users. This prevents attackers from intercepting sensitive data.
- Higher Authentication for Sensitive Operations: For actions that involve sensitive information or critical functions, like deleting data or processing payments, require stronger authentication (such as multi-factor authentication or special permissions).
3. Versioning Your APIs
When you update your API with new features or security improvements, it’s important to manage different versions properly. Versioning allows you to make changes without breaking the existing applications that are using the older versions of your API.
- Example: If you release version 2 of your API but some users are still using version 1, you can maintain both versions (like https://yourapi.com/v1/resource and https://yourapi.com/v2/resource) to ensure that everything continues to work smoothly. This also helps you apply security patches to specific versions without affecting others.
By following these principles, you can design your APIs to be more secure and better protected from potential threats while ensuring they remain flexible and easy to manage.
Tools and Technologies for API Security
1. API Security Testing Tools
To make sure your API is secure, you need tools to test for vulnerabilities and potential weaknesses. Here are some useful tools you can use:
- OWASP ZAP: This is a free tool that helps you find security issues in your API. It can automatically scan your API for common vulnerabilities, like injection attacks or security misconfigurations.
- Postman with Security Tests: Postman is a popular tool for testing APIs. In addition to regular API testing, you can set up security tests to check for things like authentication errors or unexpected data access.
- Burp Suite: This is a powerful tool used to scan for API vulnerabilities. It helps you identify security flaws, such as broken authentication or data leaks, by simulating attacks on your API.
2. API Management Platforms
These platforms help you manage, monitor, and secure your API from a central place. They handle things like authentication, rate limiting, and logging:
- Apigee: A tool that helps you manage APIs by enforcing security policies, managing access control, and monitoring usage. It allows you to secure your API while also making it easy to scale.
- Kong: Kong is another popular platform that secures your API by managing access control, setting up rate limiting, and logging API activity. It’s designed to handle large-scale APIs.
- AWS API Gateway: This tool from Amazon Web Services helps you manage APIs by controlling who can access them and applying security features like authentication and monitoring. It’s especially useful if your API is hosted in the AWS cloud.
3. Threat Detection and Monitoring
Once your API is live, it’s important to continuously monitor its activity to detect any suspicious behavior or potential threats. These tools can help:
- DataDog: A monitoring tool that helps you track API performance and detect any unusual or malicious activity, such as unauthorized access attempts or performance slowdowns.
- Splunk: A tool that collects and analyzes data from your API, allowing you to spot any security issues or anomalies. It helps you monitor for threats in real-time.
- CloudTrail: If you’re using AWS, CloudTrail helps track every API call made in your environment. It records who accessed your API, what they did, and when they did it, which helps you detect and respond to threats quickly.
By using these tools and platforms, you can better secure your APIs, monitor their performance, and quickly identify any security threats.
API Security in the Cloud
Cloud-Specific API Security Challenges
When your APIs are hosted in the cloud, there are a few extra security challenges you need to think about:
- Shared Responsibility Model: In the cloud, security is a shared responsibility between you and your cloud provider. This means the cloud provider (like AWS or Google Cloud) handles the security of the infrastructure (like servers and networks), while you are responsible for securing your APIs, data, and applications. Understanding where your responsibility begins is key to ensuring proper security.
- Hybrid Environments (Cloud and On-Prem): Many companies use both cloud-based services and on-premises (in-house) systems. Managing security across these environments can be tricky because you have to secure both your cloud-based APIs and your on-prem systems, ensuring they communicate securely without any weak points.
Security Best Practices in Cloud-Based APIs
To keep your APIs secure in the cloud, here are some best practices you can follow:
- Use Identity and Access Management (IAM): IAM is a tool that helps control who can access your APIs and what they are allowed to do. With IAM, you can set rules for different users or services, making sure only authorized people or systems can interact with your API. For example, you can ensure that only specific employees or apps can access sensitive API functions.
- Employ Cloud-Native Security Tools: Cloud providers offer tools designed specifically to protect your APIs. For example:
- AWS Shield: This tool helps protect your APIs from DDoS (Distributed Denial of Service) attacks, where attackers flood your API with traffic to overwhelm it.
- Google Cloud Armor: This tool protects your APIs from various types of attacks by blocking suspicious traffic and keeping your API secure from threats like SQL injection or cross-site scripting (XSS).
By understanding these cloud-specific challenges and using the right tools, you can better secure your APIs and protect your applications in the cloud environment.
You May Also Read: 12 Best Practices to Secure Your API in the AWS Cloud
The Future of API Security
AI and Machine Learning for API Security
Artificial Intelligence (AI) and Machine Learning (ML) are changing the way we approach API security. These technologies help make security smarter and more efficient:
- Predictive Analytics: AI can analyze large amounts of data from your API and look for patterns that might indicate a security risk. For example, it can detect unusual behavior, like a user suddenly making too many API requests, and predict when an attack might happen before it causes damage.
- Automated Threat Detection: Machine Learning can automatically identify new and emerging threats by continuously learning from past attacks and security breaches. This means your API security can improve over time, becoming more effective at stopping attacks without needing constant manual updates.
Zero Trust Security Models
In the past, once users or systems were trusted, they were allowed to access many parts of an API. With the Zero Trust model, the idea is that you should never trust anyone or anything by default, even if they are inside your system.
- “Never Trust, Always Verify”: This means that every user, system, or device trying to access your API must be continuously verified, no matter where they are. For example, even if a user is inside your network, they still need to provide proof (like multi-factor authentication) every time they try to use sensitive API functions.
- Continuous Monitoring: APIs following the Zero Trust model are constantly monitored for any suspicious activity, ensuring that no one can access more than they should, and that any potential threat is detected right away.
Shift-Left Security
Shift-Left Security means thinking about and addressing security earlier in the development process, rather than waiting until the end.
- Incorporating Security Early: Instead of testing your API for security issues only after it’s built, you should start incorporating security practices at the beginning of the development cycle. This includes adding security tests to your code as it’s written, reviewing API design for security flaws early, and making sure everyone on the development team understands security best practices.
By shifting security “left” (earlier in the process), you can catch and fix security issues before they become bigger problems later on. This saves time and effort while making your APIs much more secure from the start.
You May Also Read: How to Choose the Right API Development Company
Conclusion
APIs are essential for modern applications but can pose security risks like unauthorized access, data breaches, and DDoS attacks if not properly protected. Optimizing API security is crucial to safeguarding your applications and user data. Best practices include using OAuth 2.0 for authentication, HTTPS for encryption, rate limiting to prevent overloads, and securing endpoints. Tools like API gateways, web application firewalls (WAFs), and cloud-based security can help enhance protection. API security is an ongoing effort, helping you stay resilient against evolving threats.
Concerned about API vulnerabilities? Our API development and integration services ensure your applications are safeguarded against threats. Contact us today to learn how we can help enhance your API security.
















