How to Secure Your Intellectual Property When Outsourcing?
Table of Contents
Outsourcing software development can be a great way to scale your business, tap into global talent, and save costs. However, it also comes with risks – especially when protecting your intellectual property (IP). Your IP is one of your most valuable assets, and ensuring it stays secure during software development outsourcing is crucial to avoid potential misuse or breaches.
Working closely with outsourcing partners is essential to address these risks. Whether choosing a partner for custom software development or modernizing your legacy systems, you should focus on establishing clear agreements, implementing strong security protocols, and maintaining constant oversight. Eager to know various ways to secure your IP during software development outsourcing? Read the blog.
Importance of Intellectual Property Rights
When outsourcing software development, protecting your intellectual property (IP) is crucial. Your ideas, code, and data are the foundation of your business, and losing control of them can have serious consequences. Without proper safeguards, your IP could be misused, stolen, or exposed to legal risks. By understanding the potential challenges and putting measures in place, you can protect your business and ensure your software development process runs smoothly. Here’s why IP protection matters and the key risks to watch out for:
- Unauthorized Access and Theft
Sharing sensitive information with software outsourcing companies can leave your IP vulnerable to unauthorized access or theft. To minimize this risk, you should use secure access protocols, limit data sharing to what’s necessary, and monitor vendor activities closely. - Ownership Disputes
Without clear contracts, ownership disputes over the developed software can arise. Specify in your agreement that you own the code, designs, and other deliverables created for your project. This avoids confusion and ensures you retain full rights. - Code Reuse by Vendors
Vendors may reuse your proprietary code in other projects, diluting your competitive edge. Including specific clauses in your contract prohibiting code reuse ensures that your software remains unique and exclusive to your business. - Lack of Legal Protections in Vendor’s Country
Some countries may lack strong IP laws, making it harder to address misuse or theft. Partner with outsourcing companies in regions with robust legal protections or include jurisdiction-specific clauses to ensure you’re covered legally. - Subcontracting Risks
Software outsoucring companies sometimes subcontract work without informing clients, increasing the chances of IP misuse. Make it clear in your contract that subcontracting requires your prior approval so you can control who has access to your project. - Inadequate NDAs and Legal Agreements
Weak or unclear NDAs and contracts leave your IP exposed. Work with legal experts to draft agreements that clearly define IP ownership, confidentiality, and breach penalties. Comprehensive documents are key to protecting your rights. - Reverse Engineering Risks
Reverse engineering allows others to recreate your software without authorization. Protect your software with anti-reverse engineering techniques, and ensure your agreements include restrictions on unauthorized use or distribution. - Data Breaches
Sharing sensitive data with a software outsourcing partner can lead to breaches if their security measures are insufficient. Check the vendor’s data protection protocols, require regular security audits, and include data security clauses in your agreement. - Software Licensing Issues
Using unlicensed tools or components in your project can lead to legal or financial penalties. You should ensure the vendor uses licensed software and that all rights are clearly defined in your contract to avoid these risks. - Unsecured Development Environments
Developing software in unsecured environments can expose your project to unauthorized access. You should focus on secure development environments with encryption, access controls, and regular security assessments to protect your IP.
You May Also Read: Balancing Cost & Quality in Software Development Outsourcing
Types of Intellectual Property in Software Development
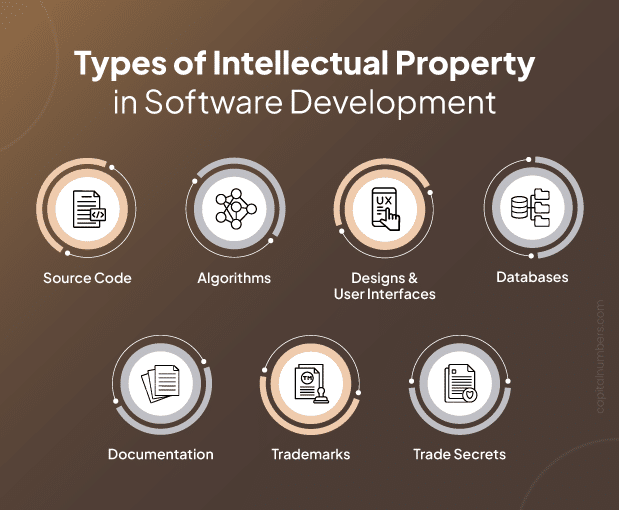
When developing software, it is essential to identify and protect various types of intellectual property that contribute to your product’s uniqueness and value. These include:
- Source Code
The source code is the backbone of your software. It contains the instructions written by developers to make your application function. Protecting source code ensures your software’s functionality and uniqueness remain exclusive to your business. - Algorithms
Algorithms define the logic and processes behind your software’s operations. They are critical for functionality and efficiency. Securing algorithms prevents competitors from copying the unique logic that powers your application. - Designs and User Interfaces
The look and feel of your software, including layouts, buttons, and colors, are part of your IP. A well-designed user interface enhances user experience and distinguishes your software from competitors. - Databases
Databases store valuable information, such as customer data or operational records. Protecting databases ensures that the structure and content remain secure and inaccessible to unauthorized users. - Documentation
Documentation includes manuals, guides, and technical specifications that explain how your software works. Protecting these ensures that your proprietary knowledge remains confidential and isn’t misused. - Trademarks
Trademarks cover branding elements like your software’s name, logo, or tagline. They help users identify your product and protect your brand identity from being copied or misused by others. - Trade Secrets
Trade secrets include any confidential practices or processes that give your software a competitive edge, such as unique methods or proprietary tools. Safeguarding trade secrets ensures that your competitive advantage is maintained.
Top 10 Ways to Safeguard Your IP When Outsourcing
If you’re wondering how to protect your intellectual property when outsourcing, follow these tips:
1. Choose the Right Offshore Development Partner
Partnering with a trusted offshore development company is critical for protecting your IP. Verify that they comply with international data security standards like GDPR or ISO certifications or are SOC 2 Type II certified. A right offshore development partner should also have a strong track record and clear policies on confidentiality and data protection.
You May Also Read: Capital Numbers Achieves the Prestigious SOC 2 Type II Certification
2. Use Comprehensive Legal Agreements
Legal agreements are your first line of defense. Ensure the vendor signs key contracts such as Non-Disclosure Agreements (NDAs) to protect sensitive information and Intellectual Property Rights Agreements to clarify ownership of deliverables. Include Work-for-Hire Agreements to transfer ownership of any created work to your business. Also, a Master Service Agreement (MSA) and Service Level Agreement (SLA) should define the scope of work, deliverables, timelines, and penalties for breaches. These agreements provide a robust legal framework to safeguard your IP throughout the project.
3. Retain Full Ownership of Deliverables
Ensure your contract explicitly states that all deliverables, including source code, designs, and documentation, belong to your company. This avoids disputes and guarantees you have rights to use, modify, or distribute the software. Collaborate with legal experts to include clauses that protect your ownership and prevent any ambiguity.
4. Streamline Offshore Development
Establish clear workflows, milestones, and communication protocols to ensure alignment between your team and the vendor. Streamlining the offshore software development process reduces risks like errors, miscommunication, or IP mishandling. Use detailed project plans, set measurable goals, and conduct regular status meetings to ensure everyone is on the same page.
5. Limit Access to Sensitive Information
You should restrict access to critical data by sharing only what’s necessary for each task. Implement multi-factor authentication (MFA) and secure file-sharing platforms to protect sensitive information. Also, maintain a detailed log of who accesses your data and ensure strict accountability among the vendor’s team.
6. Use Project Management Tools
Transparency and oversight are crucial when outsourcing. Project management tools are essential for tracking progress, assigning tasks, and ensuring compliance with your IP protection guidelines. Platforms like Trello, Jira, or Asana let you monitor activities, enforce deadlines, and maintain detailed records of all communications and deliverables.
7. Conduct Regular Security Audits
Regular security audits are vital to ensure your vendor follows best practices for safeguarding your intellectual property. These audits help identify potential vulnerabilities, assess security protocols, and verify that proper measures are in place to protect your data. By conducting routine evaluations, you can address risks early and ensure your IP remains secure throughout the development process.
8. Protect Data with Encryption and Security Protocols
Implement advanced data protection methods such as encryption for all sensitive files and secure communication channels like HTTPS and SSL/TLS. Ensure the vendor also follows protocols for secure data storage, backups, and disaster recovery. Regularly test these security measures to confirm their effectiveness.
9. Manage Subcontracting Risks
Subcontracting can expose your IP to unauthorized third parties, creating additional risks. You should include clauses in your agreement that require vendors to seek written approval before subcontracting any aspect of the project. Demand that subcontractors follow the same IP protection standards, and maintain transparency throughout the process to mitigate risks.
10. Address Employee Turnover at the Vendor Side
High employee turnover on the vendor side can increase the risk of data leaks or IP misuse. Discuss the vendor’s onboarding and exit protocols to ensure proper handling of sensitive information. Choose offshore development partners with strong employee retention policies and a proven track record of maintaining confidentiality to safeguard your IP effectively.
You May Also Read: Don’t Get Hacked: Essential Software Security Checklist for Developers
Final Words
Securing intellectual property during software development outsourcing is critical to protecting your business’ assets. You can effectively reduce risks and keep your IP secure by carefully selecting the right partner, implementing solid legal agreements, and maintaining strong security measures.
Besides, regular monitoring and access control are key to ensuring sensitive information stays protected throughout the process. With the right approach, you can take full advantage of outsourcing while ensuring your intellectual property remains safe and your business relationships are built on trust.














