Cybersecurity in the Digital Age: Protecting Your Web Applications from Threats
Table of Contents
Cybersecurity must be addressed in a digital world where technology has become integral to daily life. With the growth of digital platforms and considering the sophisticated nature of cyber threats, people and organizations need to prioritize cybersecurity. As we move into the digital age, cybersecurity is becoming increasingly important, and we will examine some key reasons why it should be a priority for everyone to focus on in this blog post.
What does cybersecurity mean?
Cybersecurity is protecting computer systems and networks from illegal access, damage, or inaccessibility through mitigating information risks and vulnerabilities. Unauthorized access, interception, usage, disclosure, and data deletion are all potential threats to information.
Types of cybersecurity
- Network Security
- Application Security
- Cloud Security
Network security: the roots of cybersecurity
Before the rise of the web, cloud, and mobile, cybersecurity was focused mostly on systems and network security. The physical approach to IT security focuses on hardware and infrastructure, including servers, workstations, routers, switches, firewalls, and wired/wireless communication. This includes all communication protocols below the application layer. Traditionally, network security relied on perimeter defense and a physically secure internal network to prevent external attacks.
Network security aims to prevent unauthorized usage of devices, systems, and services. To safeguard hardware and software assets, prepare an inventory and check for known vulnerabilities using CVE numbers. Security experts can patch vulnerabilities and shut down services using scan results and best practices to prevent network issues. Network security relies on updating and maintenance rather than identifying new vulnerabilities, as environments have become mostly stable once configured.
Network security requires physical and software-based defenses, such as firewalls and intrusion prevention systems (IPS). To achieve effective security, put these devices in appropriate network locations and implement rules to prevent intrusions while permitting valid traffic. Before the cloud, perimeter defense involved restricting users and business systems to a secure internal network and filtering Internet communication—vulnerability scanning and resolution in network security.
Vulnerability scanning and resolution in network security
- Use a network scanner to identify hardware and software assets.
- Identify devices, systems, exposed ports, and services.
- Verify assets for known vulnerabilities, configuration issues, outdated releases, policy compliance, etc.
- Provide scan findings for verification.
- Repair, upgrade, or patch susceptible assets.
Application security
Web application development prioritizes security (Web AppSec) to guarantee that web applications perform properly, even when attacked. The notion refers to a set of security rules built into a Web application to protect its assets from potentially hostile agents. Web applications, like any software, inevitably have flaws. Some of these flaws represent vulnerabilities that can be exploited, posing threats to companies. Web application security protects against such flaws. It entails utilizing secure development approaches and deploying security measures throughout the software development life cycle (SDLC), ensuring that design faults and implementation issues are resolved.
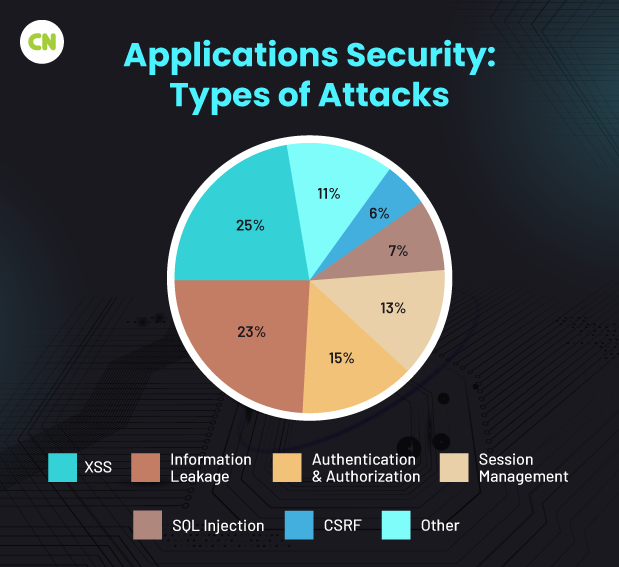
Types of attacks:
1 SQL injection:
Websites link to databases using SQL or Structured Query Language. SQL allows a website to save, delete, retrieve, update, and build databases. Furthermore, SQL keeps user transaction information and logs it on a website.
When a SQL injection occurs, hackers use the database’s search queries to exploit weaknesses.
A hacker, for example, could enter ‘or 1=1’ instead of a standard username and password. If a website includes this string in a SQL command to check for user existence in a database, the query will return “true”. As a result, a hacker can get access to a vulnerable location.
Solution:
Given hackers’ ability to use automated tools for SQL injection, it is critical in custom software development to filter user input carefully. Programming languages have capabilities that ensure correct filtration of user input.
2 XSS attacks:
XSS, or Cross-Site Scripting, is an attack that involves introducing JavaScript code into web pages as hyperlinks.
When users click on such a hyperlink, their data can be taken, the adverts on the website can be changed, and the entire session can be hijacked.
XSS scripts are difficult to detect because hackers embed them in social media posts, comments, suggestions, and reviews as important information that entices users to click.
Solution:
Because hackers can implant malicious codes as user inputs on social media, web forums, and websites where users are most likely to click, website owners must guarantee that user input is properly vetted and malicious codes are removed.
3 DDoS attacks:
DDoS, or Distributed Denial of Service, assaults occur when malware-infected computers send data requests to your website.
In most situations, the computer owner is unaware that their machine is being utilized to overload a website’s server.
Hackers utilize dozens of these computers to overwhelm a server, causing the website to crash.
In certain circumstances, hackers demand exorbitant ransom payments to restore the website’s functionality.
Solution:
To counteract DDoS assaults, you must implement filtration mechanisms that drop malicious, spoofed, and malformed packets from unknown sources. Also, develop an aggressive policy for connection timeouts. If you’re utilizing firewalls, be sure they have DDoS protection.
4 CSRF attacks:
Cross-Site Request Forgery, or CSRF, is a sort of harmful attack used by hackers after they have accessed a web application.
A hacker can provide unauthorized commands from a user’s account and deceive the web application into accepting them. The main disadvantage of these assaults is that no barrier can prevent hackers from transferring payments and gaining sensitive account information and user data.
You must be wondering how CSRF differs from XSS. The primary distinction is that CSRF attacks occur after gaining account access. Unlike XSS, a hacker has all the necessary credentials to claim an account here.
Solution:
To safeguard against CSRF attacks, inspect HTTP headers to determine whether the request originates from an application or an external source.
5 DNS spoofing:
DNS spoofing attacks attempt to shift website traffic from a legitimate site to a malicious one.
Hackers utilize this approach to gather information about where traffic is being rerouted. The main disadvantage of this assault is that neither the website owner nor the user will be aware that their connection has been stopped and moved to an unauthorized site.
Following redirection, customers are deceived into giving sensitive data such as bank account information, credit/debit card numbers, and phone numbers to steal their data.
Solution:
To avoid DNS spoofing, set a TTL (Time-To-Live) or hop limit to shorten the duration of computer data. Also, regularly clean DNS captures from your machine.
6 Social engineering attacks:
In addition to enticing consumers and website administrators to provide their data, social engineering attempts are on the rise.
These are some of the most common social engineering attacks.
Phishing emails
In a phishing assault, emails imitating a brand’s identity are sent to users, leading them to believe they are from a legitimate source.
Once confidence has been created, emails requesting contact information, bank account numbers, and addresses are sent on behalf of a legitimate organization. They may even ask you to click unsolicited links containing dangerous downloads.
Baiting
Baiting is a popular type of social engineering attack. Hackers can display files containing vital information, such as money hacks or free OTT platform access. When you click on them, harmful codes are automatically downloaded to your system.
Pretexting
In such attacks, hackers mimic a client or employee and contact or text you, requesting important bank, username, password, or company information.
Solution:
The only way to prevent these attacks is to teach workers and raise customer knowledge about them. Educating people about them makes them more likely to understand the hazards.
7 Non-targeted attacks:
As the name implies, these assaults do not aim to compromise your website.
You must be asking what the goal of these attacks is.
These assaults target web hosting and CMS platforms rather than single websites. They believe in seizing large guns rather than fighting foot soldiers.
Non-targeted attacks compromise CMS platforms such as WordPress and Joomla by targeting an out-of-date version.
Because not all websites are kept up to date, hackers utilize automated bots to identify old websites that make simple targets for them.
Solution:
The answer to preventing non-targeted attacks is straightforward. Keep your plugins, CMS platforms, and hosting software up to date.
8 Memory corruption:
Memory corruption occurs when hackers change a memory area to install uninvited and malicious software.
Hackers can also use that software to gain access to all devices, networks, and programs associated with that machine.
Solution:
To avoid memory corruption, run an anti-malware scan regularly. If your memory has already been corrupted, replace the faulty memory.
9 Buffer storage:
A buffer overflow occurs when data containing malware is overwritten several times in a storage place, particularly in target memory space.
Because data multiplies in storage, so does dangerous content. As a result, more vulnerabilities emerge in the system.
Solution:
To prevent buffer storage, carefully assess your codes. Also, include objective quantifiers in your code.
Cyberattacks can have major consequences for your reputation if they are not mitigated. Customers prefer to leave their data in secure hands. By proactively addressing and preventing cyber risks, you can maintain the trust of customers who entrust their important data to you.
Cloud security
Cloud security is a set of procedures and technology intended to address internal and external risks to enterprise security. Organizations require cloud security as they implement their digital transformation strategy and integrate cloud-based tools and services into their infrastructure.
Cloud security risks:
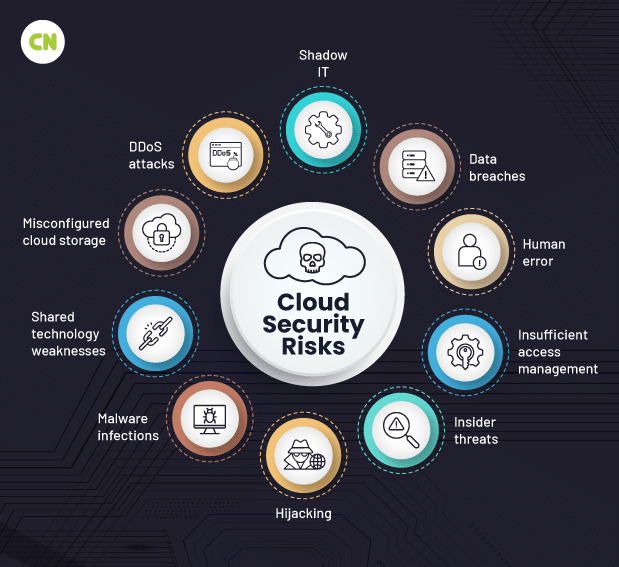
You cannot eliminate danger; only manage it. Knowing the common hazards ahead of time will help you deal with them in your environment.
- Unmanaged attack surface
- Human error
- Misconfiguration
- Data breach
1 Unmanaged attack surface
An attack surface represents your entire environment’s exposure. The use of microservices might result in an explosion of publicly available workloads. Each task contributes to the attack surface. Without close supervision, you risk exposing your infrastructure in ways you don’t realize until an assault.
Nobody wants that late-night call.
The attack surface may also contain subtle information leaks that lead to an attack. For example, CrowdStrike’s threat hunters discovered an attacker who used sampled DNS request data collected over public WiFi to determine the names of S3 buckets. CrowdStrike stopped the attempt before the attackers could cause any damage, but it’s a perfect example of risk’s omnipresent nature. Even strict constraints on S3 buckets were insufficient to mask their existence. As long as you use the public Internet or cloud, you are automatically exposing an attack surface to the entire globe.
Your business may require it to function, but keep an eye on it.
2 Human error
According to Gartner, human error will account for 99% of all cloud security failures between now and 2025. Human mistake is an unavoidable risk while developing business apps. However, hosting resources in the public cloud increases the danger.
Because of the ease of usage of the cloud, users may be accessing APIs that you are unaware of, allowing gaps in your perimeter to open up. Manage human error by implementing robust controls to help individuals make the right judgments.
One final rule: don’t blame others for mistakes. Blame the process. Create protocols and guidelines that help people do the right thing. You will need more than pointing fingers to help your business become more secure.
3 Misconfiguration
Cloud settings expand as providers introduce new services over time. Many firms use more than one provider.
Providers have varied default configurations, and each service has its implementations and nuances. Until enterprises become skilled in safeguarding their numerous cloud services, enemies will continue to exploit misconfiguration.
4 Data breaches
A data breach happens when sensitive information leaves your hands without your knowledge or consent. Data is more valuable to attackers than anything else; hence, it is the target of most attacks. Misconfiguration of the cloud and a lack of runtime protection might render it vulnerable to theft.
The impact of data breaches varies according to the type of data stolen. Thieves sell personally identifiable information (PII) and personal health information (PHI) on the dark web to individuals looking to steal identities or send phishing emails.
Other sensitive information, such as internal documents or emails, could be exploited to harm a company’s reputation or devalue its shares. Regardless of the motive for the data theft, breaches continue to pose a significant threat to cloud-based enterprises.
How to manage cloud security risks?
Follow these guidelines to mitigate risk in the cloud:
- Conduct regular risk assessments to identify new risks.
- Document and review any risks you choose to accept.
Cloud security threats:
A threat is an attack against your cloud assets to exploit a vulnerability.
-
Zero-day exploits
“Cloud” means “someone else’s computer.” However, you will be vulnerable to zero-day exploits if you use computers and software, even if they are hosted in another organization’s data center.
Zero-day exploits exploit vulnerabilities in popular software and operating systems that the manufacturer has not patched. They’re risky because even if your cloud configuration is top-notch, an attacker can use zero-day flaws to obtain access to the environment.
-
Advanced persistent threats
An advanced persistent threat (APT) is a sophisticated, long-term cyberattack in which an intruder establishes an unnoticed presence in a network and steals critical data over time.
APTs are not rapid “drive-by” attacks. The attacker remains in the environment, moving from workload to workload, looking for sensitive information to steal and sell to the highest bidder. These assaults are risky because they may begin with a zero-day exploit and remain undiscovered for months.
-
Insider Threats
An insider threat is a cybersecurity threat that originates within the organization, typically from a current or former employee or another person with direct access to the company network, sensitive data, and intellectual property (IP), as well as knowledge of business processes, company policies, or other information that could aid in the execution of such an attack.
-
Cyberattacks
A cyberattack is an attempt by cybercriminals, hackers, or other digital enemies to gain access to a computer network or system, typically to modify, steal, destroy, or expose data.
Malware, phishing, DoS and DDoS assaults, SQL injections, and IoT-based attacks are all common types of cyberattacks against businesses.
How to handle cloud security threats?
There are numerous specialized attacks to protect against, making it difficult to keep up with them all. However, here are three suggestions for securing your cloud assets from these and other dangers.
- Use secure coding standards while creating microservices.
- Ensure your cloud configuration is complete and free of errors.
- After establishing a strong base, focus on proactive threat hunting.
Conclusion
Network security and web application security are two distinct yet complementary components of the cybersecurity puzzle. Each pertains to a distinct technology and faces different risks. To remain secure in today’s connected world, firms must maintain a strong cybersecurity posture in both domains, especially since online applications account for the majority of cyberattacks and data breaches.
For a software development company to maintain a strong security posture in a cloud(Web)-based ecosystem, it is critical to install proper tools and procedures across all aspects of IT security. Network and system security remain critical components of any comprehensive security program, but the front line of the struggle against cyber crime has firmly shifted to online security. Organizations cannot afford to quit, especially with so much at stake if a hack succeeds.